For financial gain, hackers exploit ransomware through which they encrypt victims’ data and then demand a ransom payment in exchange for its release.
It shows the urgency and importance of the compromised data, as they compel victims to pay to regain access or prevent the sensitive data from being exposed or deleted.
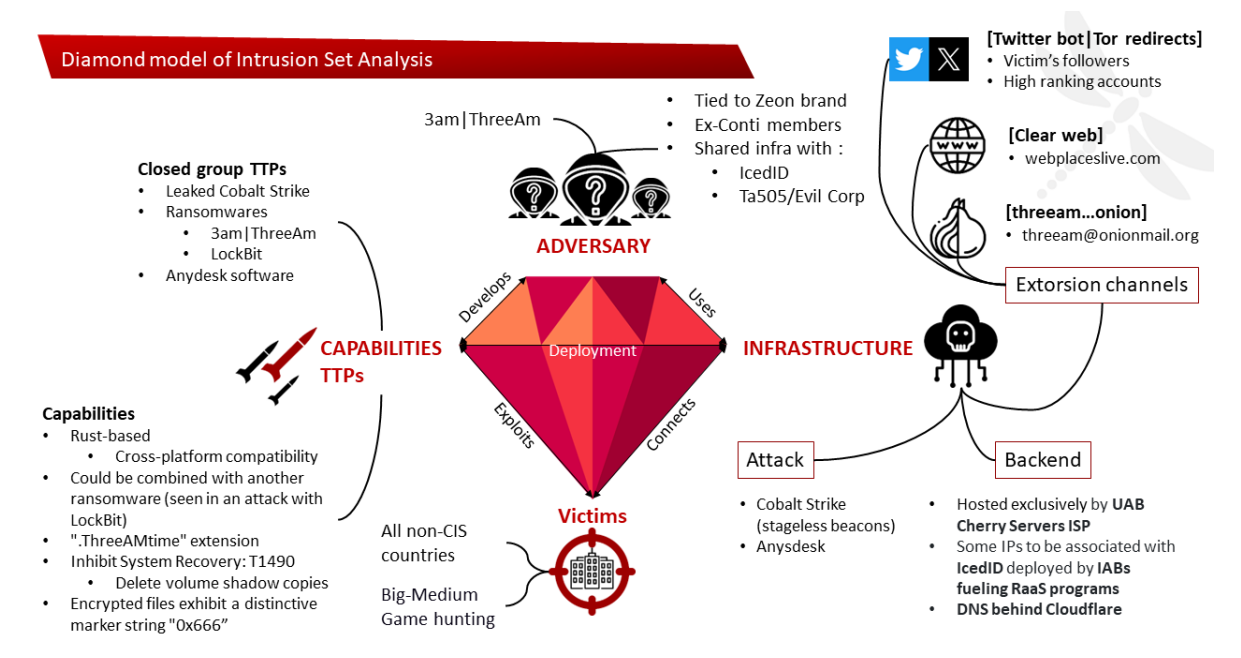
Security analysts at Intrinsic recently discovered ThreeAM (aka 3 AM, ThreeAMtime) ransomware, which has been actively attacking small and medium companies.
Open Suspicious Files & Links in the ANY RUN Sandbox Safely; Try All Features for Free. Understand malware behavior, collect IOCs, and easily map malicious actions to TTPs — all in our interactive sandbox.
ThreeAM Ransomware Campaign
ThreeAM exposes victim data on a leak site if ransoms aren’t paid, and this ransomware is linked to ex-Conti members’ R&D, which is now Royal.
While the ThreeAM is less sophisticated, it could have a significant attack impact. It uses X/Twitter bots and Rust language for ransomware, which makes it a new malware family.
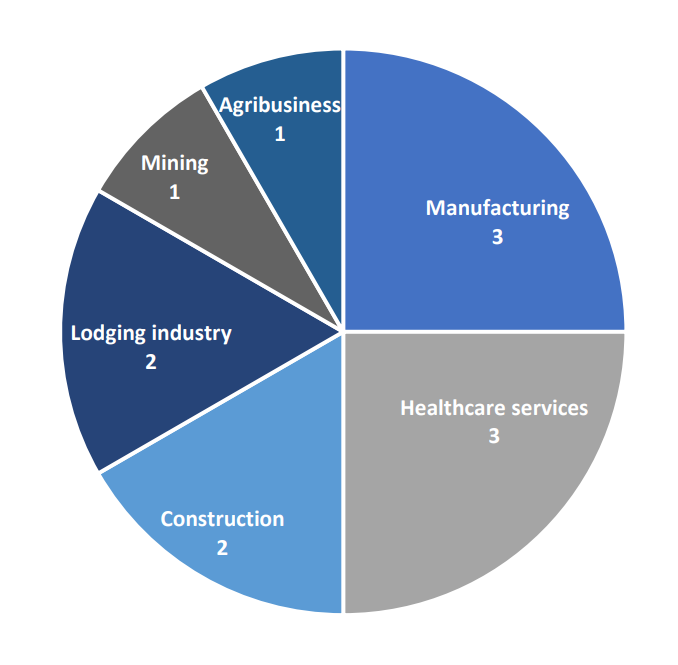
ThreeAM ransomware hit a dozen US businesses from September 13 to October 26, 2023. Targeting small to medium enterprises in which 10 victims had a maximum of 50 employees and less than $5 million in revenue.
SMEs are vulnerable due to limited resources. Neuraxpharm, which is a European pharmacy leader with 1,000 employees, also fell victim.
The versatile victimology aligns with evolving ransomware tactics favoring mid-size businesses. Trellix’s June 2023 report highlights the US businesses as the most likely ransomware targets.
Symantec unveiled ThreeAM ransomware linked to ex-Conti-Ryuk-TrickBot nexus. It’s a Rust-based threat that is emerging as a fallback for failed LockBit deployments.
Royal ransomware leader ‘Baddie’ has ties to Evil Corp, and LockBit was adopted by both for evasion. ThreeAM, with rare sightings, hints at future attacks. It uses Rust for efficiency and evasion.
The ransomware erases Volume Shadow copies and appends ‘.ThreeAMtime’ extension to encrypted files. Notably, encrypted files have a unique marker string, ‘0x666.’ The evolving landscape shows ransomware groups adopting diverse tactics and collaboration attempts.
ThreeAM’s blog surfaced on Shodan at IP 5.199.174[.]149, and the analysis reveals 27 servers with the same Apache banner hosted by ‘UAB Cherry Servers.’ Six IPs stand out and are found to be sharing commonalities.
Domains use ‘llc’ to mimic US entities, and the infrastructure links to ALPHV/BlackCat and IcedID malware. ThreeAM blog also points to IP 5.199.173[.]56, which is close to the first IP. The TLS is secured with a Let’s Encrypt certificate; it hosts a WordPress CMS.
One domain, wirelessrepaid626[.]com, was linked to Formbook and phishing in July 2022. ThreeAM’s ransomware relies on IP 85.159.229[.]62. It used a Cobalt Strike beacon with stageless injection, similar to Cring ransomware tactics.
The payload, a “260.6 KB” DLL compiled around 2019-12-05, aligns with the TTPs of exConti and LockBit. ThreeAM also uses X for communication, with the account ‘ThreeAM1st’ created on August 10, 2023.
ThreeAm operators run a name-and-shame blog on TOR, which is active in double extortion. A Google dork revealed a clear web version using the contact email. The blog matched with victim INTECH and is currently inactive, but it may reappear.
The top-tier ransomware ecosystem is evolving rapidly, and to counter such threats, proactive security measures are a must and essential.
Read the full article here

