Malvertising campaigns often trick victims with near-perfect replicas of software vendor sites.
To easily trick their victims and achieve their malicious purposes, threat actors target popular software vendors like-

Cybersecurity researchers at Malwarebytes recently identified a malicious campaign that mimics the WindowsReport[.]com portal to distribute a malicious CPU-Z installer. The targeted site attracts geeks and admins seeking:-
- Computer reviews
- Computer tips
- Computer software
In this malicious campaign, hackers actively target Windows users with malicious ads to deliver malware.
Hackers Trick Windows Users
Threat actors replicated the content of Windows Report for deceptive purposes, but the portal is still secure.

This is part of a broader malvertising campaign targeting utilities like:-
Besides this, cybersecurity analysts at Malwarebytes have already alerted Google about this incident for an immediate takedown.
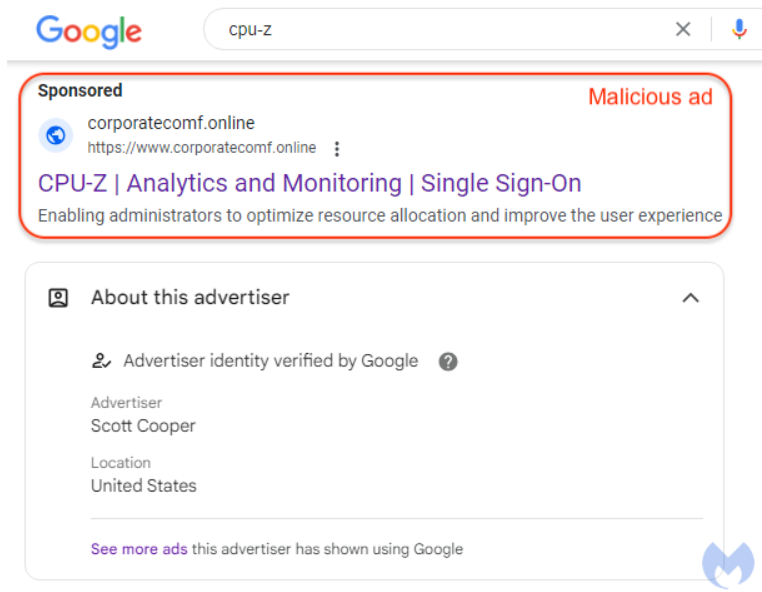
An advertiser using Scott Cooper’s likely spoof or hacked name appears in a misleading advertisement for the Windows program CPU-Z.
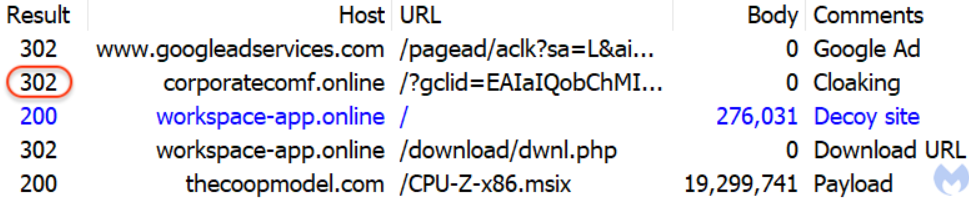
Threat actors use cloaking to evade detection. While the non-target clicks show a standard blog, for victims, the “corporatecomf[.]online” site redirects to “workspace-app[.]online.”
A mimic domain, resembling WindowsReport[.]com, deceives users searching for CPU-Z. The download page may seem legitimate, but the URL doesn’t match.
Several domains are hosted at the IP address 74.119.192.188 as part of malvertising activities. Apart from this, a malicious PowerShell script, along with the FakeBat loader, is included in the payload, which is a signed MSIX installer.
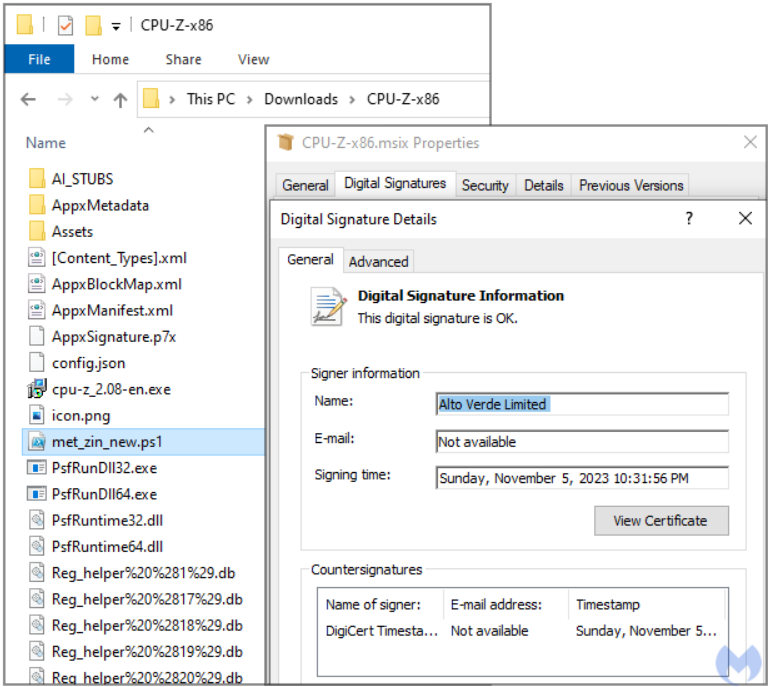
The actor mimicked Windows Report as users often download utilities from such sites. Legitimacy is increased by the signed MSI installer, and by replacing a PowerShell script, MSI loaders provide simple modifications to the final payload.
In enterprises, verifying a file’s checksum through its SHA256 hash sum can ensure it’s flawless, matching the website of the vendor.
StorageGuard scans, detects, and fixes security misconfigurations and vulnerabilities across hundreds of storage and backup devices.
IOCs
Ad Domains
- argenferia[.]com
- realvnc[.]pro
- corporatecomf[.]online
- cilrix-corp[.]pro
- thecoopmodel[.]com
- winscp-apps[.]online
- wireshark-app[.]online
- cilrix-corporate[.]online
- workspace-app[.]online
Payload URLs
- thecoopmodel[.]com/CPU-Z-x86.msix
- kaotickontracting[.]info/account/hdr.jpg
- ivcgroup[.]in/temp/Citrix-x64.msix
- robo-claim[.]site/order/team.tar.gpg
- argenferia[.]com/RealVNC-x64.msix
Payloads
- 55d3ed51c3d8f56ab305a40936b446f761021abfc55e5cc8234c98a2c93e99e1
- 9acbf1a5cd040c6dcecbe4e8e65044b380b7432f46c5fbf2ecdc97549487ca88
- 419e06194c01ca930ed5d7484222e6827fd24520e72bfe6892cfde95573ffa16
- cf9589665615375d1ad22d3b84e97bb686616157f2092e2047adb1a7b378cc95
C2s
- 11234jkhfkujhs[.]site
- 11234jkhfkujhs[.]top
- 94.131.111[.]240
- 81.177.136[.]179
Patch Manager Plus, the one-stop solution for automated updates of over 850 third-party applications: Try Free Trial.
Read the full article here