A hacker attack on a supply chain can be highly dangerous as it can disrupt the flow of goods and services, causing widespread economic and operational damage.
Such attacks pose a serious risk to companies and society at large since they can result in:-

- Monetary losses
- Harm to one’s reputation
- Endanger public safety
This year, a software vendor fell victim to Lazarus malware through unpatched software despite prior warnings and patches. However, security analysts at Securelist proactively detected and stopped a similar attack on another vendor.
Researchers at Kaspersky have discovered that Lazarus, a persistent threat actor, has repeatedly targeted a software vendor. Their aim was to steal the vendor’s source code and compromise their software supply chain.
Infection Timeline
Threat actors showed advanced skills with SIGNBT malware for control. While the memory held Lazarus’ LPEClient, used for profiling and payloads in past attacks on the following industries:-
Here below, we have presented the infection timeline:-
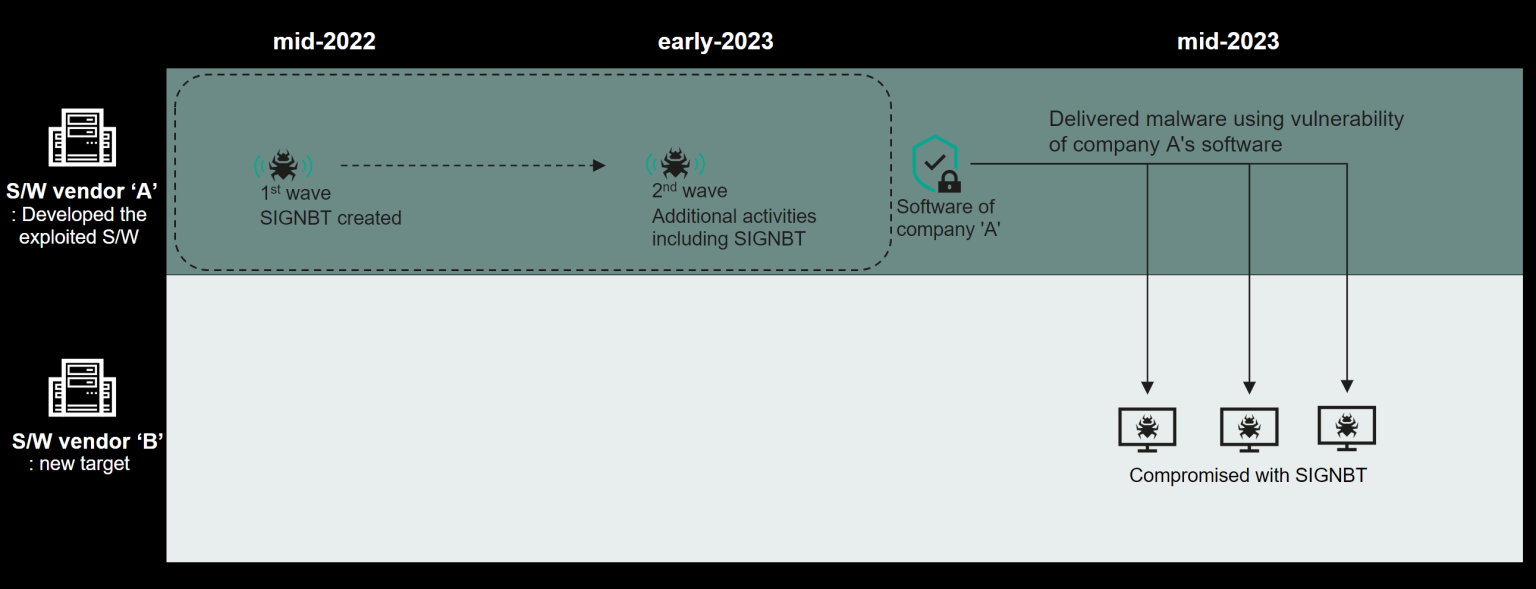
Software Vendor Compromised
Security analysts detected many attacks in July 2023 via web security software exploitation. In July 2023, researchers detected attacks via web security software exploitation. The exact method remains unknown, but they found SIGNBT malware in the software’s memory, establishing persistence with tactics like creating:-
- ualapi.dll file
- side-loading legitimate files
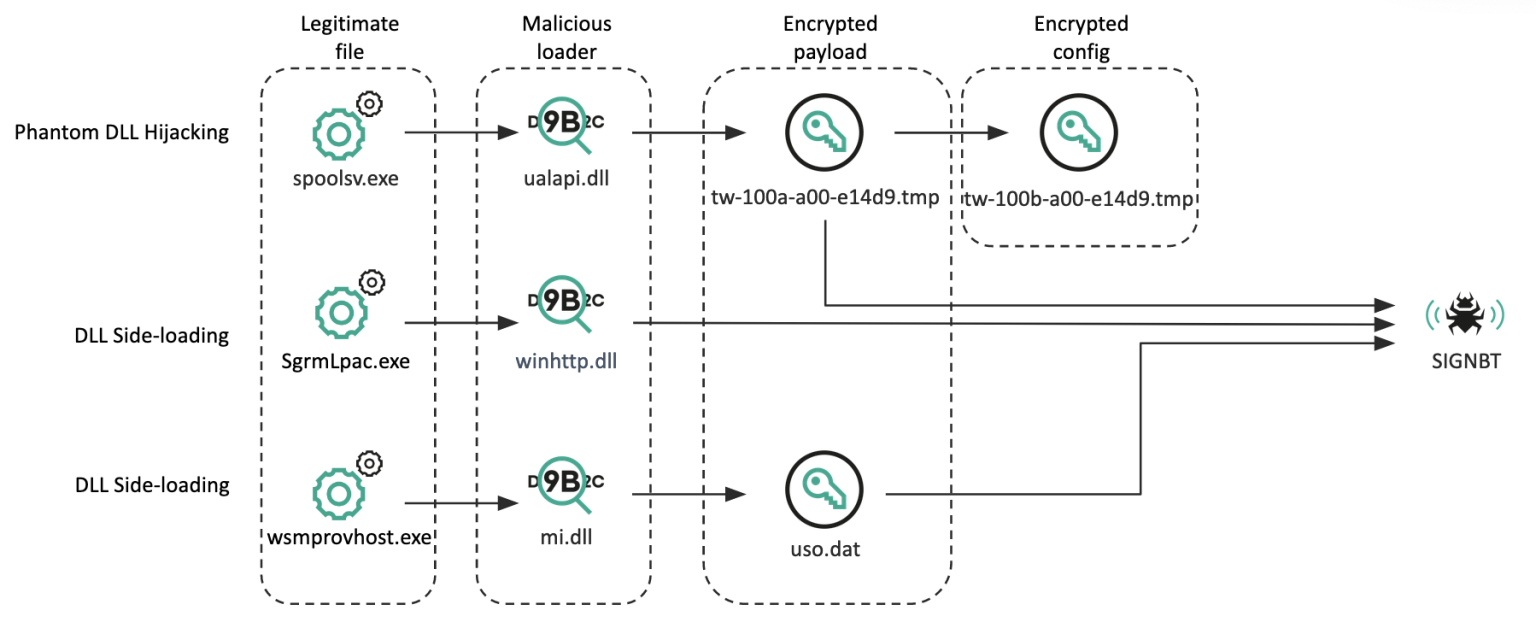
Lazarus often hijacks spoolsv.exe and uses ualapi.dll, as this technique is similar to Gopuram malware.
They create ualapi.dll with Shareaza Torrent Wizard code, verifying the victim using MachineGuid. If matched, the malware proceeds to the next step, reading the payload from a specific file path.
The loader decrypts SIGNBT with a key from tw-100a-a00-e14d9.tmp, then reads a config file.
The first 32 characters of the base64-encoded string in the file serve as an AES key for decryption. The config contains C2 addresses, sleep intervals, and other critical parameters.
SIGNBT malware primarily operates in memory via a loader. It communicates with a C2 server, using unique SIGNBT strings and varying prefixes for verification at different C2 stages.
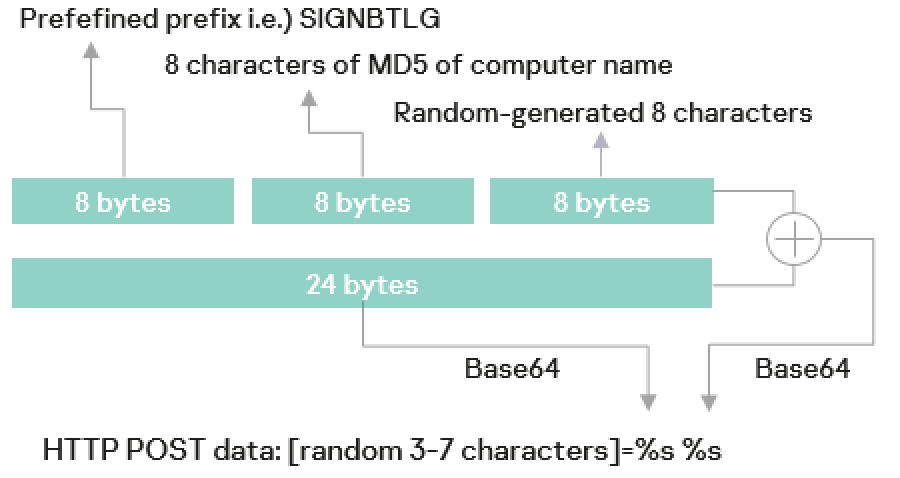
Here below, we have mentioned all the prefixes used:-
- SIGNBTLG
- SIGNBTKE
- SIGNBTGC
- SIGNBTFI
- SIGNBTSR
The malware crafts a 24-byte value, XORs it with random data using a 24-byte key, and then encodes both with base64. It adds random HTTP parameter names, making its C2 communications hard to analyze.
The malware validates C2 responses with an “XOR success” check. If successful, it gathers the victim’s computer info and then sends data with the SIGNBTGC prefix, decrypting using an AES key from SIGNBTLG. If “keep,” it responds with “OK”; otherwise, it uses SIGNBTFI to report issues in C2 communication.
The actor deploys additional memory-resident malware like LPEClient and credential dumpers.
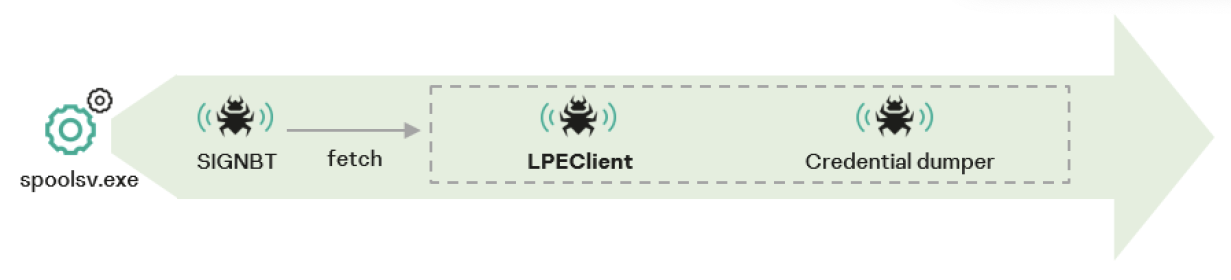
LPEClient was discovered in 2020, gathers info, and downloads payloads for in-memory execution, now with improved stealth tactics, showing threat actor evolution.
Lazarus Group, a versatile threat actor, exploits high-profile software vulnerabilities and spreads malware efficiently, transcending industries and geographic boundaries with sophisticated methods and persistent motivation.
Protect yourself from vulnerabilities using Patch Manager Plus to patch over 850 third-party applications quickly. Try a free trial to ensure 100% security.
Read the full article here

