Cybersecurity is constantly changing and facing new challenges. One of them is the fake Chrome update malware, which has been around for several years and is still active.
This malware pretends to be a genuine Chrome browser update, but it is a remote access trojan (RAT) that can take over your computer.

This is often the first step in a ransomware attack, which can cost you much money and data. Security experts have noticed a new version of this malware, called “FakeUpdateRU” by Jerome Segura of MalwareBytes.
This is not the same as the old SocGholish malware, but a new one made by a different group of hackers. They are trying to take advantage of the high demand for ransomware.
Many other groups like them have appeared recently. Google has acted quickly and blocked most websites that spread this malware.
You will see a warning page from Google if you try to visit them. The malware changes the main index[.]php file of the websites’ themes.
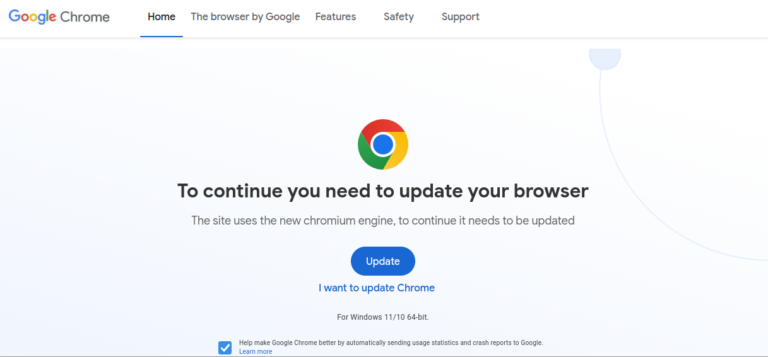
Fake Chrome Update Page
The fake Chrome update page looks very similar to the real one. One thing that stands out is that the malware files are made of plain HTML code taken from the UK English version of Google’s website.
This shows that the hackers used a Chrome (Chromium-based) browser to make the malware. But this also causes some Russian words to appear in the files, even for users who don’t use Chrome.
The hackers have changed some words on the fake update page, such as “Download” to “Update,” to trick users into thinking they need to update their browsers.
The real danger is in the JavaScript code at the bottom of the page, which starts the malware download when users click on the “Update” button.
This code uses a Chrome-themed domain to get the final download URL, usually on another hacked website.
The malware belongs to the Zgrat and Redline Stealer malware families, known for ransomware attacks.
The fake update pages and the malware files are on different hacked websites.
The hackers use many domains with similar names to send users to the malware .ZIP file, and they register them often.
You can tell which websites are infected by looking for a special Google Tag Manager script, which shows how big this campaign is.
Google has been fast in blocking domains that redirect users, so the hackers have changed their method and now link directly to downloads on other hacked websites.
This means they have to infect all those websites again instead of changing one file on their server.
Some new versions of the malware have removed most of the Russian words from the fake update pages, which means the hackers are changing their tactics.
The worrying thing is that some infected websites have JavaScript code that talks to a temporary Telegram channel.
“The hackers probably use this to get notified when someone downloads their malware. Telegram’s encryption and other features make it a good tool for hackers,” reads the Sucuri report.
To avoid these fake Chrome update malware, experts advise updating plugins and themes, making WordPress websites more secure and strong, and backing up data regularly.
Using a firewall can also stop infections. If a website might be infected, it is important to act fast, and there are skilled security experts who can help in removing infections and protecting the site.
Protect yourself from vulnerabilities using Patch Manager Plus to patch over 850 third-party applications quickly. Try a free trial to ensure 100% security.
Read the full article here

