Cloud Security Podcast — Two Years Later or Our Year-End Reflections for 2022!
We have been running our Cloud Security Podcast by Google for almost 2 years (TWO YEARS!) and since we are on a break now, I wanted to reflect a bit, while Tim is relaxing on a beach somewhere warm and “hammy” 🙂
So, we aired 102 episodes, but what was new in 2022?
- We explored a few new areas of cloud security. We often express disdain towards the saying “cloud is just someone else’s computer”, and we like to amend it to “cloud is not *JUST* someone else’s computer.” So we went and explored SaaS security in “EP99 Google Workspace Security: from Threats to Zero Trust” and “EP76 Powering Secure SaaS … But Not with CASB? Cloud Detection and Response?”
- We seem to have removed the curse of AI — namely that our first 2 episodes on securing AI (“EP52 Securing AI with DeepMind CISO” and “EP68 How We Attack AI? Learn More at Our RSA Panel!”) just didn’t land well. And then “EP84 How to Secure Artificial Intelligence (AI): Threats, Approaches, Lessons So Far” really did. More securing AI and perhaps AI for security episodes coming!
- Some of our most popular episodes are still the ones about “How Google does something cool in security” (“EP75 How We Scale Detection and Response at Google: Automation, Metrics, Toil”, and “EP71 Attacking Google to Defend Google: How Google Does Red Team” are our favorite examples, but we have many more). Many more of this are coming, some are even already recorded
- For our main conference (Google Cloud Next 2022), we did something different again: we ran 4 episodes daily during the event, but with each episode being good listening on its own too.
- We supported worthy initiatives like #ShareTheMicCyber (“Sharing The Mic In Cyber with STMIC Hosts Lauren and Christina: Representation, Psychological Safety, Security”)
- We had some really high-minded episodes (“EP67 Cyber Defense Matrix and Does Cloud Security Have to DIE to Win?”) and some lightweight fun as well.
- We also learned who makes a great guest: somebody with a triad of subject knowledge + high energy + ability to structure thoughts in audio (choose any 2 of these 3, and you will get a decent guest instead)
- Ah, and we sort of had Robert Herjavec on the show (“EP63 State of Autonomic Security Operations: Are There Sharks in Your SOC with Robert Herjavec”) and, no, this didn’t make us famous too ;-
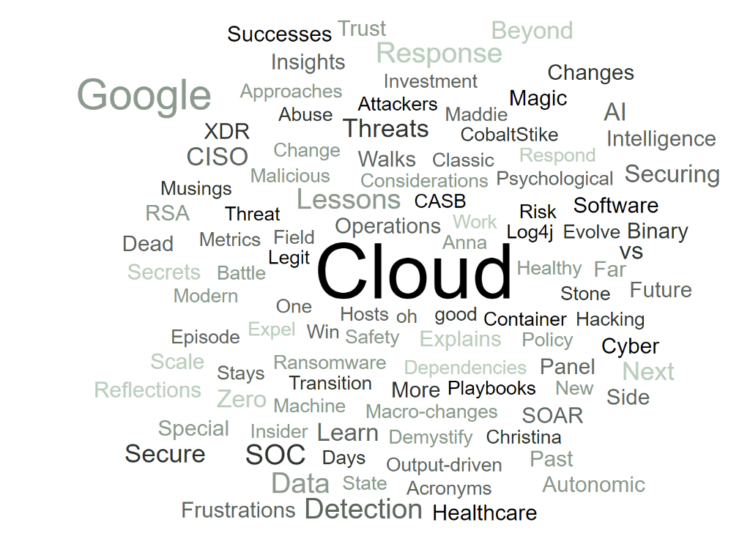
Here is how 2022 word cloud of episode titles looks like
(src)
What to expect from us in 2023?
- A weekly podcast episode and a few specials here and there — of course!!!
- Perhaps a live video of our recording session — that will be fun! Should we post the audio to YouTube, BTW?
- Some stuff that is coming in Q1 2023 includes episodes on BeyondProd, our security guardrail magic, security architecture (with more cloud migration challenges!) and a curious episode on our approach to vulnerability management. More “CISO meets cloud” episodes are planned as well!
- The 2023 season opener on January 9 would be epic as well … because Mandiant!
Now, let’s look at our basic metrics:
Top 5 episodes overall so far:
- “Confidentially Speaking“ (ep1)
- “Data Security in the Cloud“ (ep2)
- “Megatrends, Macro-changes, Microservices, Oh My! Changes in 2022 and Beyond in Cloud Security” (ep47)
- “Automate and/or Die” (ep3)
- “How We Scale Detection and Response at Google: Automation, Metrics, Toil“ (ep75)
Share your favorites in comments or on social media (LinkedIn, Twitter)?
We also understand that 102 episodes is a lot and that we cover many topics in a wide field of cloud security. So, if you want to cherry pick, here are some fun playlists (on Spotify):
So, a call to action:
- Any more playlists you want to see (share ideas on LinkedIn, Twitter)?
- Any new topics to cover?
- Fun guests to invite?
- Subscribe via Google, Spotify, Apple or your app of choice!
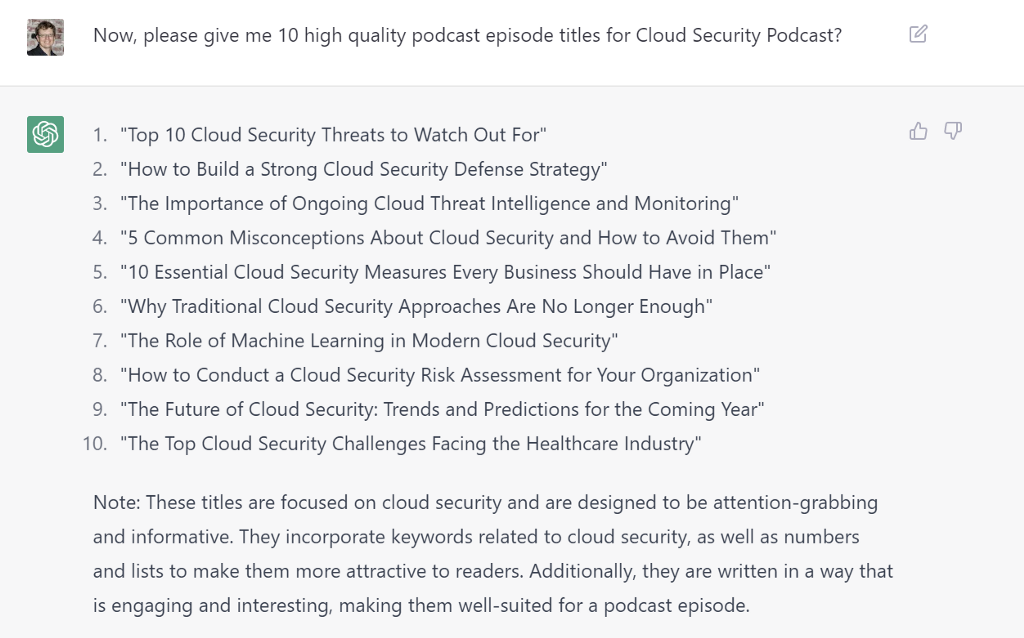
P.S. Of course we asked the future AI overlords about what we should do next, here are the answers.
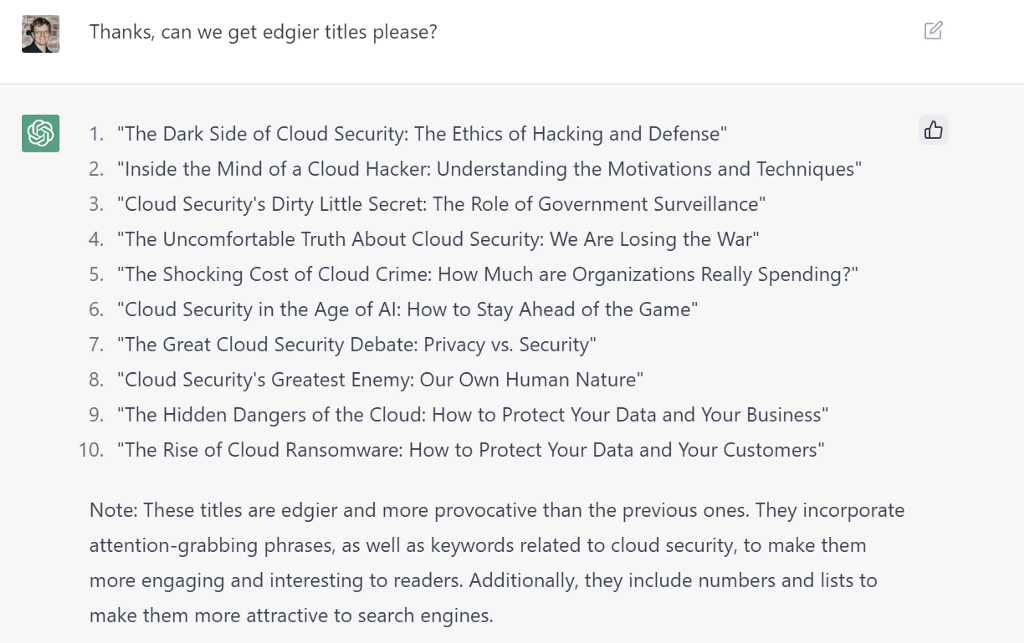
And of course, we are us, so here is what we did next:
🙂
Related:
Cloud Security Podcast — Two Years Later or Our Year-End Reflections for 2022! was originally published in Anton on Security on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from Stories by Anton Chuvakin on Medium authored by Anton Chuvakin. Read the original post at: https://medium.com/anton-on-security/cloud-security-podcast-two-years-later-or-our-year-end-reflections-for-2022-22c9e5386655?source=rss-11065c9e943e——2
Read the full article here