According to reports, the threat group known as “Nobelium” who were responsible for the SolarWinds attacks is now discovered to be targeting Microsoft tenants through the new Cross-Tenant Synchronisation (CTS) feature introduced by Microsoft.
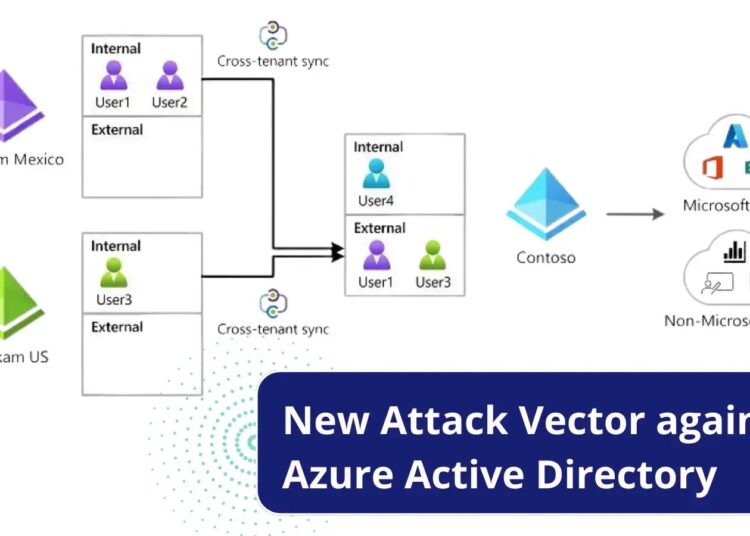
CTS is a feature that enables organizations to synchronize users and groups from other source tenants and can grant them access to the target tenant.
CTS feature also helps in creating, updating, and deleting AD (Active Directory) users across other tenants.
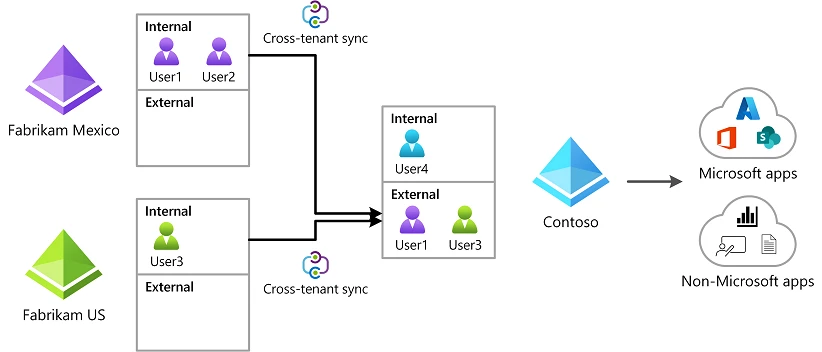
However, since this feature opens the gate to multiple tenants from one tenant, it is important to configure and manage correctly.
Misconfiguration can lead to threat actors using this feature for lateral movement across multiple tenants and performing malicious activities.
The attack from threat actors however requires licence and compromising of a privileged account or privilege escalation on a compromised tenant.
However, if a Global admin account is compromised, it is extremely easy for an attacker to deploy a backdoor and maintain persistent access to the tenants. The CTS tenants get synced through “Push” and not “Pull”.
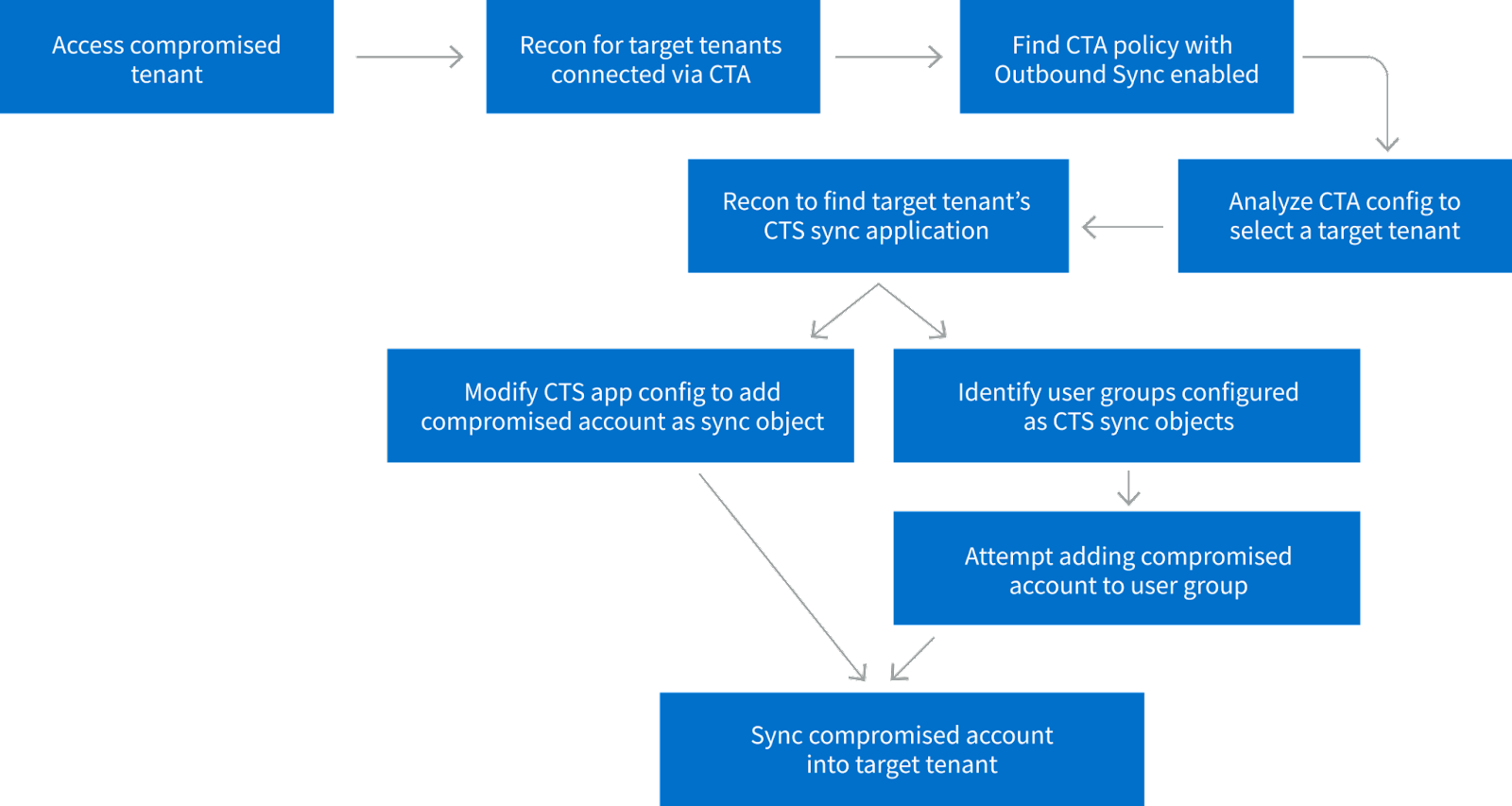
Lateral Movement
Once the threat actor compromises a tenant, it is possible for him to move laterally to other connected tenants. This can be done by reviewing the Cross Tenant Access Policies configured on the compromised tenant.
Once the threat actor finds a tenant with Outbound sync enabled, he can use that tenant to get synchronized with the target tenant.
After this, the threat actor can discover the CTS host sync application and use it to push the user account to that tenant which grants access to the target tenant.
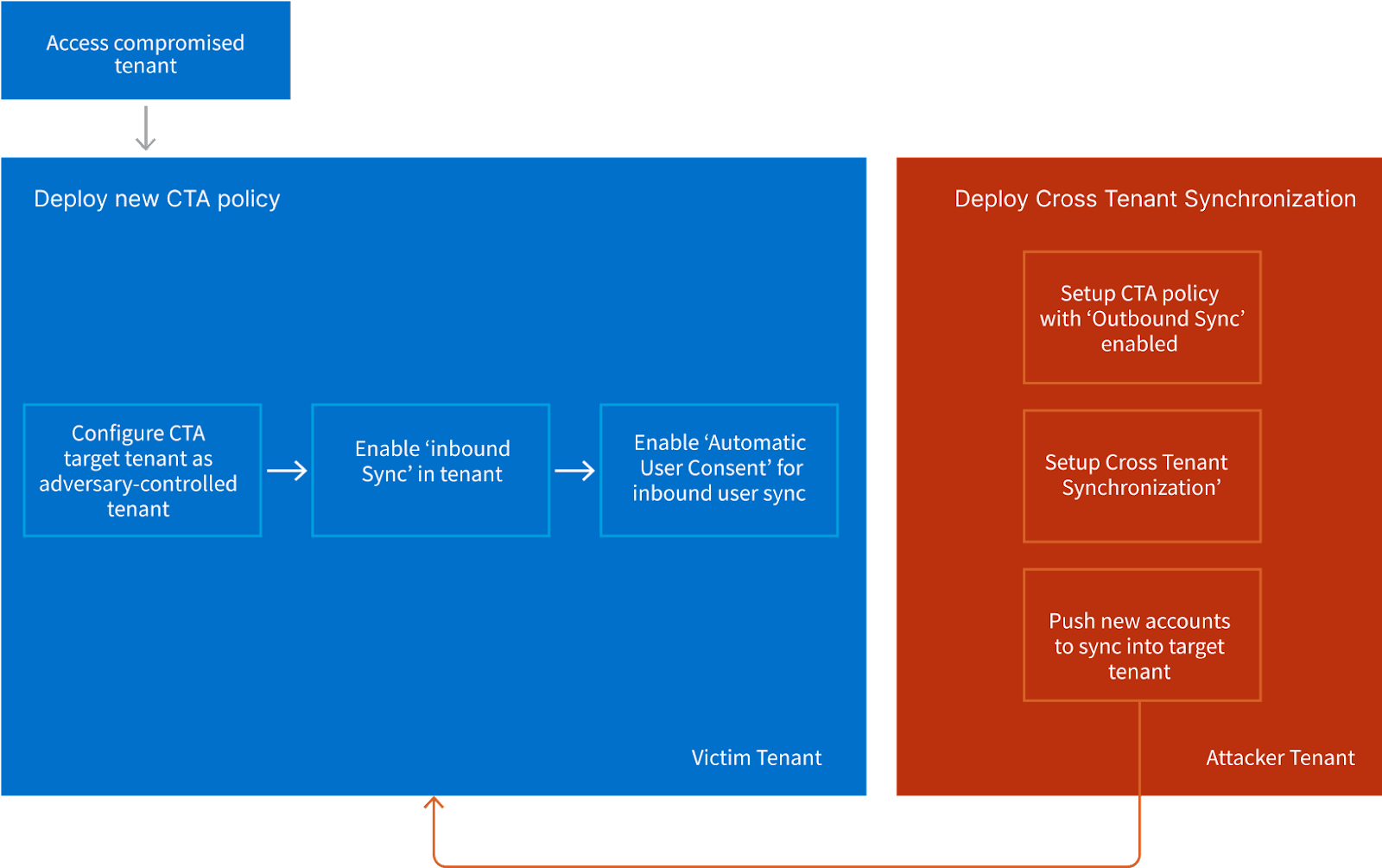
Backdoor
The attacker can then deploy a rogue Cross Tenant Access Configuration for maintaining persistent access on the compromised tenant. In addition, the attacker can also configure this to an external tenant with the help of the documentation provided by Microsoft.
A complete report on the lateral movement and backdoor has been published by Vectra which shows detailed information on this attack vector.
Users of Active Directory and Cross Tenant Synchronisation features are advised to configure them properly in order to prevent threat actors from exploiting them.
Keep yourself informed about the latest Cyber Security News by following us on GoogleNews, Linkedin, Twitter, and Facebook.
Read the full article here