Cyber Attack Trends: 2022 Mid-Year Report takes a closer look at how cyberattacks have intensified and been elevated as state – level weapon with hacktivism flourishing in the first half of this year with key predictions around attacks in the Metaverse and Supply Chain
With the war in Ukraine dominating the headlines in the first half of 2022, its impact on the cyber space has been dramatic in both scope and scale, as cyberattacks have become firmly entrenched as a state level weapon, unprecedented levels of state-sponsored attacks, the growth of hacktivism and even the recruitment of private citizens into an “IT Army.”
In the 2022 Cyber Attacks Mid-Year Report, we take a closer look at how cyber warfare has intensified to become an essential part of the preparation for, and conduct of, actual military conflict with fallouts for governments and enterprises all over the world, even those that are not directly involved in the conflict. We also explore a crossover with cyber warfare and state-affiliated hacktivism to disrupt everyday lives of citizens and cause real harm to citizens, best illustrated by the attack on the entire country of Costa Rica, which crippled essential services including healthcare and inland revenue, stopping medical appointments and the collection of taxes in this new method of ‘Country Extortion’, making ransomware the number one threat in the second half.
The report also explores top predictions for the second half highlighting :
- Ransomware’s fragmented ecosystem – while ransomware groups have become more structured and operate like regular businesses, with set targets to hit, we think, there will be many small-medium groups going forward, instead of a few large groups like the Conti group, a lesson learned as their size and power garnered too much attention, and led to its downfall.
- More diverse email infection chains – with internet macros blocked by default in Microsoft office, more sophisticated malware families will accelerate the development of new infection chains, with different file types that are password protected to prevent detection, as sophisticated social engineering attacks increase.
- Hacktivism will continue to evolve – hacktivist groups will continue to align their attacks with the agenda of their chosen nation state, particularly as the Russia-Ukraine war is still ongoing.
- Continued attacks on decentralized blockchain networks with expected first attacks in Metaverse – with major incidents relating to blockchain platforms, such as a vulnerability on Rarible market place or ApeCoin Airdrop vulnerability , we expect to see continued efforts by hackers to breach and hijack crypto assets. In addition we believe that we will see initial attacks in the Metaverse that will exploit smart contract vulnerabilities.
Cyber’s theoretical potential for major disruption to civic society just got real in 2022 and in this report, we will address these trends and more aspects of the evolving threat landscape, while provide examples and statistics of real-world events, combined with best practice recommendations for organizations to avoid becoming the next victim.
Highlights of the ‘Check Point Cyber Attack Trends Mid-Year report 2022’ include:
- Russia Ukraine War – The First Hybrid War that Forced Everyone to Take Sides
- Country Extortion – Ransomware Groups Step Up to Nation State Actor Level
- Incident Response Perspective: A special chapter offers the unique perspective of the Check Point Incident Response Team (CPIRT) with real insight into attempted and successful attacks
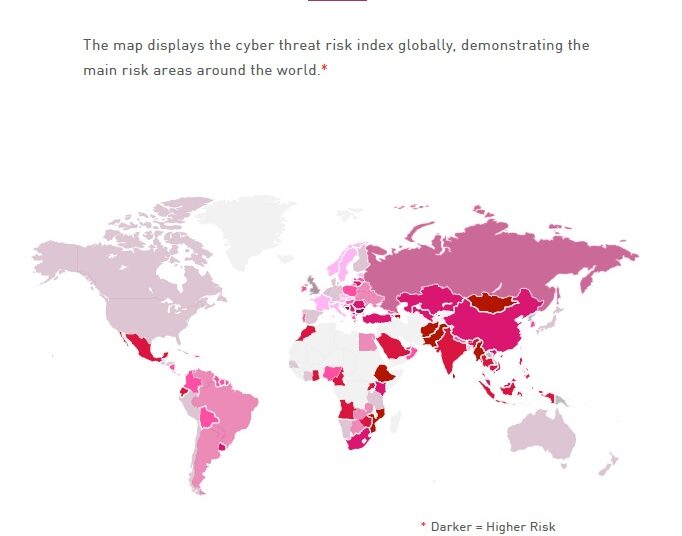
- Global threat index map: Cyber Attack categories by geographic region and by sector
- Predictions for H2 2022: What to expect and what to do to prevent the next attack
Read the full article here