Wireshark’s capabilities to analyze and monitor network traffic make it an indispensable tool for security professionals, network administrators, and even curious individuals seeking to understand the continuous communication between devices and systems.
The dependence on networks and the internet is ever-increasing in today’s interconnected world.
This growth has led to a surge in potential attack vectors and security threats.
Network pentesting examines a computer network for flaws and openings that an attacker could exploit.
A simulated network attack is conducted to identify potential security vulnerabilities and assess their exploitability for unauthorized network or resource access.
It is an essential tool for comprehending, protecting, and maintaining networks in the modern era.
Furthermore, its widespread application in penetration testing emphasizes the importance of spotting weaknesses and potential dangers to protect networked systems’ stability and security.
For example, Wireshark is one of the incident response tools that can identify potential security vulnerabilities such as unencrypted passwords and other sensitive data transmitted in clear text.
Want to Become a Master in Wireshark Network Analysis?
Learn Wireshark Network Analysis Bundle
Table of Content
What is Wireshark?
Wireshark Network Filtering
Who Created Wireshark?
Here is a brief timeline of the history of Wireshark
How to download & Install Wireshark
Common Wireshark Uses
Conclusion
What is Wireshark?
Wireshark is a powerful, open-source network analysis tool that allows users to capture and inspect network traffic. It is a powerful tool enabling users to capture, analyze, and troubleshoot network traffic.
Wireshark allows seeing what’s happening on the network at a microscopic level by analyzing the data packets flowing through the network interface. It has a user-friendly GUI with filters, color coding, graphs, and other features for traffic analysis.
Numerous protocols are supported, including IP, TCP, UDP, HTTP, SSL/TLS, FTP, DNS, DHCP, and many more.
As a result, it is possible to analyze the traffic of numerous network applications and obtain specific information about packets, such as header information, payload data, host conversations, top talkers, etc.
Wireshark can capture data from network interfaces, including Ethernet, Wi-Fi, and Bluetooth. Users can view the captured data at various levels, from high-level protocol summaries to detailed packet-level analyses.
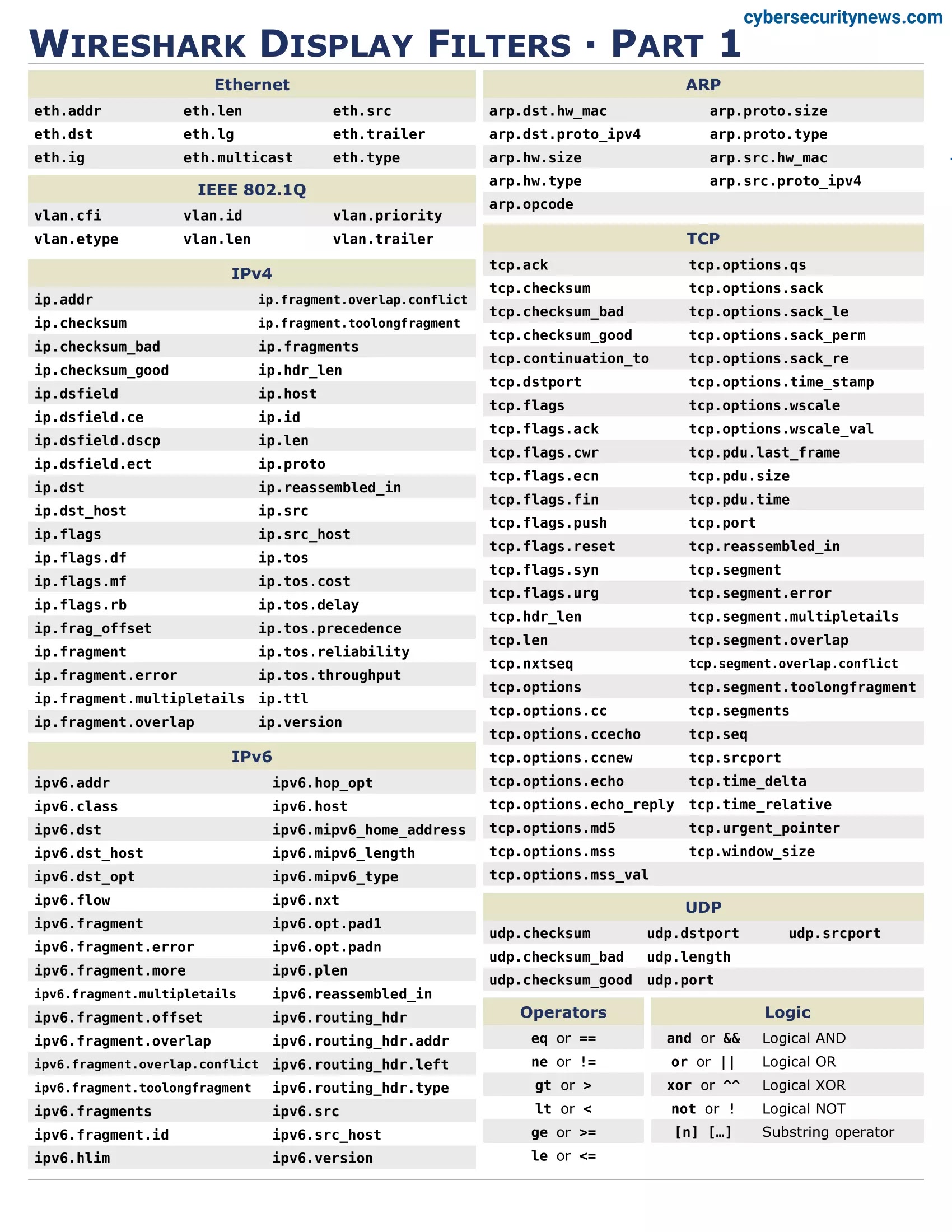
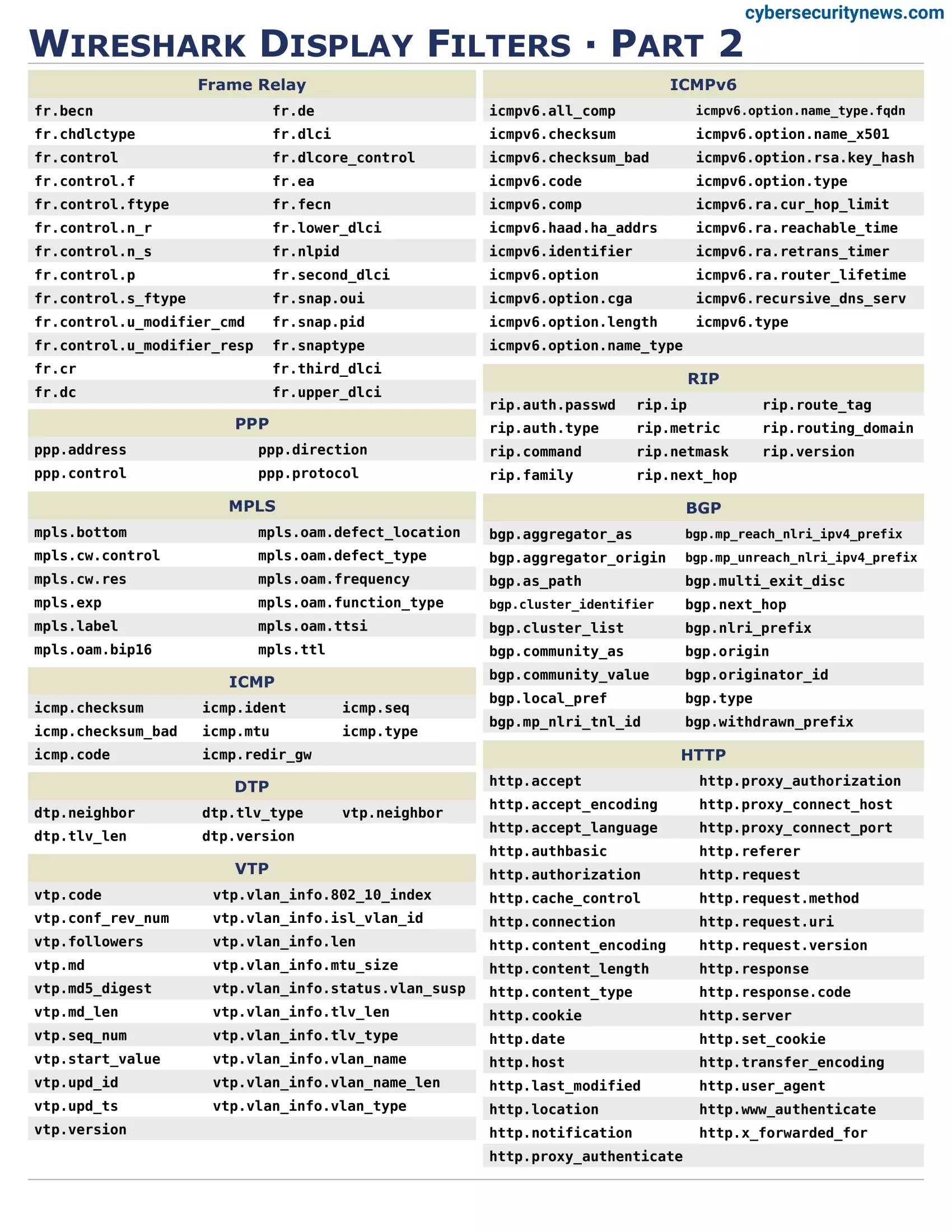
Wireshark Network Filtering
Wireshark offers several filtering and search features that simplify locating and analyzing particular network events or problems.
There are several types of filters:
- Capture filters: These filter incoming network traffic before captures it. Capture filters are based on the pcap filter syntax and can be specified in the capture options dialog box or at the command line when starting a capture.
- Display filters: These are used to filter the captured network traffic that is displayed in main window. Display filters are based on Wireshark’s display filter syntax and can be entered in the filter bar at the top of the main window.
- Protocol filters: These filter network traffic based on the protocol being used. Protocol filters are available in the “Analyze” menu and can display only traffic that uses a specific protocol.
- Conversation filters: These filter network traffic based on the conversation between two hosts. Conversation filters are available in the “Statistics” menu and display only traffic between hosts.
Some Examples of Filters in Wireshark Include:
| ip.addr == 192.168.1.1 | This filter will display only network traffic involving IP address 192.168.1.1 |
| TCP.port == 80 | This filter will display only network traffic that uses the TCP port 80, commonly used for HTTP traffic. |
| udp | This filter will display only network traffic that uses the UDP protocol. |
| http.request.method == “GET” | This filter will display only HTTP traffic that uses the GET method. |
| ip.src == 192.168.1.1 && ip.dst == 192.168.1.2 | This filter will display only network traffic between the IP addresses 192.168.1.1 and 192.168.1.2. |
Who Created Wireshark?
Wireshark was created in 1998 by Gerald Combs. Combs was a computer science graduate student at the University of Missouri-Kansas City. He was working on a project to develop a network analyzer tool to help him solve network problems.
It was initially named Ethereal but was renamed Wireshark in 2006 due to trademark issues. It is available for various platforms, including Windows, macOS, and Linux.
Wireshark is written in the C, C++, and Lua programming languages and released under the GNU General Public License. The software is constantly updated with new features, bug fixes, and security updates.
The community comprises programmers, contributors, and users who collaborate to enhance and keep the application current with the most recent network protocols and technologies.
Versions 4.0.4 and 3.6.12, made available on March 2, 2023, are Wireshark’s most recent stable versions as of April 2023.
Additionally, Tool has a development release called Wireshark-git that contains the most recent improvements and bug fixes.
Version 3.6.12 is the last release branch with support for 32-bit Windows. Therefore, updates will no longer be available for that platform after May 22, 2024.
Here is a Brief Timeline of the History of Wireshark:
- 1998: Gerald Combs creates the first version of Wireshark under Ethereal.
- 1999: Ethereal is released as open-source software under the GPL.
- 2006: Ethereal is renamed to Wireshark due to trademark issues.
- 2008: Wireshark 1.0 has a new user interface and support for more protocols.
- 2010: Wireshark 1.4 is released with improved performance and support for wireless protocols.
- 2013: Wireshark 1.10 is released with a new, more customizable user interface.
- 2015: Wireshark 2.0 is released with a new packet decoding engine and support for new protocols.
- 2019: Wireshark 3.0 has a new user interface and support for more protocols.
- 2020: Wireshark 3.3.0 Released – Updated Futures, New Protocol & Updated Capture File Support
- 2021: Wireshark 3.6 is released with improved support for 5G and other new technologies—last release to support 32-bit Windows.
- 2022: Wireshark 4.0 is released with changes in many filters and added many new protocols support.
- 2023: Wireshark 4.0.4 and 3.6.12 is released with multiple changes.
Common Wireshark Uses
Packet Analysis: Wireshark lets pentesters capture, dissect, and analyze packets in real time or from saved files. This helps understand network protocols, identify vulnerabilities, and monitor network behavior.
- Network Discovery: Penetration testers can use the tool to identify network devices, services, and topology, helping them map the attack surface and plan their penetration tests.
- Protocol Analysis: Wireshark is equipped with decoders for a wide range of protocols, which enables pentesters to analyze various network communication patterns and detect anomalies or suspicious activity.
- Sniffing Sensitive Data: it can help pentesters identify sensitive information transmitted over the network, such as passwords, session tokens, or confidential documents, which may be vulnerable to interception and exploitation.
- Reconnaissance: Itcan be used for passive reconnaissance, gathering information about targeted systems and networks without actively probing or engaging with the target.
- Forensic Analysis: In the event of a security breach, it can help security professionals analyze network traffic, identify indicators of compromise (IOCs), and understand the methods and tools used by attackers.
- Network troubleshooting: it can diagnose network problems by capturing and analyzing traffic. It can help identify network congestion, packet loss, and misconfigured network devices.
- Network security: it can detect and analyze malware, viruses, and network attacks. It can also monitor network traffic for suspicious activity and identify security vulnerabilities.
- Application analysis: Wireshark can analyze the behavior of applications that use network protocols. This can help identify performance issues and bugs in the application.
- Protocol development: it can be used to develop and test new network protocols. It can capture and decode network traffic to help developers understand how protocols are used in the real world.
- Diagnosing bandwidth issues – it can help you determine if there are any bandwidth hogs on your network by showing you a graphical view of network traffic.
How Wireshark Improves Network Security
Wireshark is an open-source packet analyzer that network professionals widely use for troubleshooting, analysis, and network security.
It can help improve network security by capturing and analyzing network traffic in several ways.
1. Identifying Unusual Network Traffic
Wireshark can identify unusual patterns or spikes in traffic that could indicate malicious activity by continuously monitoring network traffic.
For instance, a sudden increase in traffic to a particular IP address could indicate a distributed denial-of-service (DDoS) attack. Network administrators can take appropriate measures to mitigate potential threats by identifying these anomalies.
2. Detecting Intrusions and Vulnerabilities
Wireshark can detect intrusions and vulnerabilities in the network by analyzing packet data.
For instance, searching for particular packet signatures associated with these exploits can assist in identifying attempts to exploit known vulnerabilities, such as Heartbleed or EternalBlue.
Network administrators can take appropriate action to patch vulnerabilities and secure the network by detecting and analyzing these intrusions.
3. Analyzing Malware and Advanced Persistent Threats (APTs)
Security analysts can use Wireshark to dissect and analyze the communication patterns of malware and APTs to understand these threats’ behavior better and create effective countermeasures.
Analysts can find indicators of compromise (IOCs) and clean up infected systems by looking at the network traffic produced by malware.
4. Verifying Security Policies and Controls
The tool can help network administrators verify that security policies and controls are correctly implemented and functioning as intended.
For example, it can be used to monitor the effectiveness of firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) by analyzing packet data to confirm that these security measures are blocking or alerting malicious traffic as expected.
5. Troubleshooting Network Security Issues
Wireshark can diagnose and troubleshoot network security issues, such as misconfigurations or performance problems related to security tools like VPNs or encryption.
By capturing and analyzing network traffic, administrators can pinpoint the root cause of the issue and implement the necessary fixes to improve network security.
How to Download & Install Wireshark
Wireshark is available for Windows, Mac, and Linux and can be easily installed via a command line or directly launching the application.
1. Wireshark For Windows
- Double-click the installer and follow the installation wizard.
- It may ask to install WinPcap, a packet capture architecture needs during installation. Accept the installation of WinPcap.
- Once installed, it can be launched from the Start menu.
2. Wireshark For Mac
- Double-click the Wireshark disk image to mount it.
- Drag the Wireshark app from the disk image to your Applications folder.
- Follow the installation process, such as agreeing to terms and licenses.
- You can now launch it from your Applications folder or Launchpad.
Suppose you’re running Wireshark on macOS and have upgraded to macOS 13 from an earlier version. In that case, you will likely have to open and run the “Uninstall ChmodBPF” package and then “Install ChmodBPF” to reset the ChmodBPF Launch Daemon.
3. Wireshark For Linux
- On Linux, it is available through the package manager. It can be installed with:
- Ubuntu/Debian: sudo apt install wireshark
- RHEL/CentOS: sudo yum install wireshark
The above will install it and all required dependencies.
- Wireshark can then be launched from the system application menu or run the command “wireshark” in a terminal.
On some Linux distributions, it may be necessary to run the tool with sudo or add the user to the it group to capture packets.
That’s it! the tool is now installed, and analyzing network traffic can be started.
Conclusion
For network security experts, Wireshark is a vital tool because it offers in-depth insight into network traffic and assists in identifying potential threats and vulnerabilities.
As a result, organizations can strengthen their network security posture and better defend their systems and data from cyberattacks by utilizing Wireshark’s capabilities.
it assists in locating security flaws like policy violations, brute force attacks, and DoS attacks in networks.
In addition, Wireshark provides network professionals access to the raw data flowing through their networks by analyzing individual packets.
Overall, Wireshark is a crucial tool for network administrators and security experts to diagnose issues, gain visibility, and improve the security posture of their network.
Learn Master in Wireshark Network Analysis – Wireshark Network Analysis Course Bundle
Also Read:
Read the full article here