Several threat actors have already been exploiting a newly discovered Android banking trojan, dubbed Nexus, to penetrate 450 financial applications and steal data.
While this malware was identified by cybersecurity analysts at Italian cybersecurity firm, Cleafy, they affirmed that it is still in its early development stages.
However, ATO attacks against banking portals and cryptocurrency service providers can be conducted using this malware as it is equipped with all the main features.
Cleafy discovered the presence of the new Android banking Trojan known as “Nexus” in June 2022. Although Cleafy first thought Nexus was a highly dynamic variation of the previously tracked Trojan known as “Sova,” additional analysis revealed that Nexus has unique traits and capabilities.
At the time of detection, the malware was discovered to have merged numerous portions of Sova code. Not only that even it also displayed a broad variety of capabilities that allowed it to attack over 200 mobile banking, cryptocurrency, and other financial apps.
Price tag or fee

Earlier this month, cybersecurity firm Cyble documented the emergence of this new malware in several hacking forums. So, the threat actors behind this malware advertised it to potential clients as a subscription service with a monthly fee of $3,000.
As early as June 2022, at least six months before the malware was announced, there was evidence that the malware was being used in real-world attacks. It has been reported that most Nexus infections are occurring in Turkey.
Moreover, it appears to incorporate a ransomware module actively developing and reuses parts of another banking trojan named SOVA.
Countries excluded
This is interesting to note since the Nexus authors have clearly specified that their malware will not be used in any of the following countries:-
- Azerbaijan
- Armenia
- Belarus
- Kazakhstan
- Kyrgyzstan
- Moldova
- Russia
- Tajikistan
- Uzbekistan
- Ukraine
- Indonesia
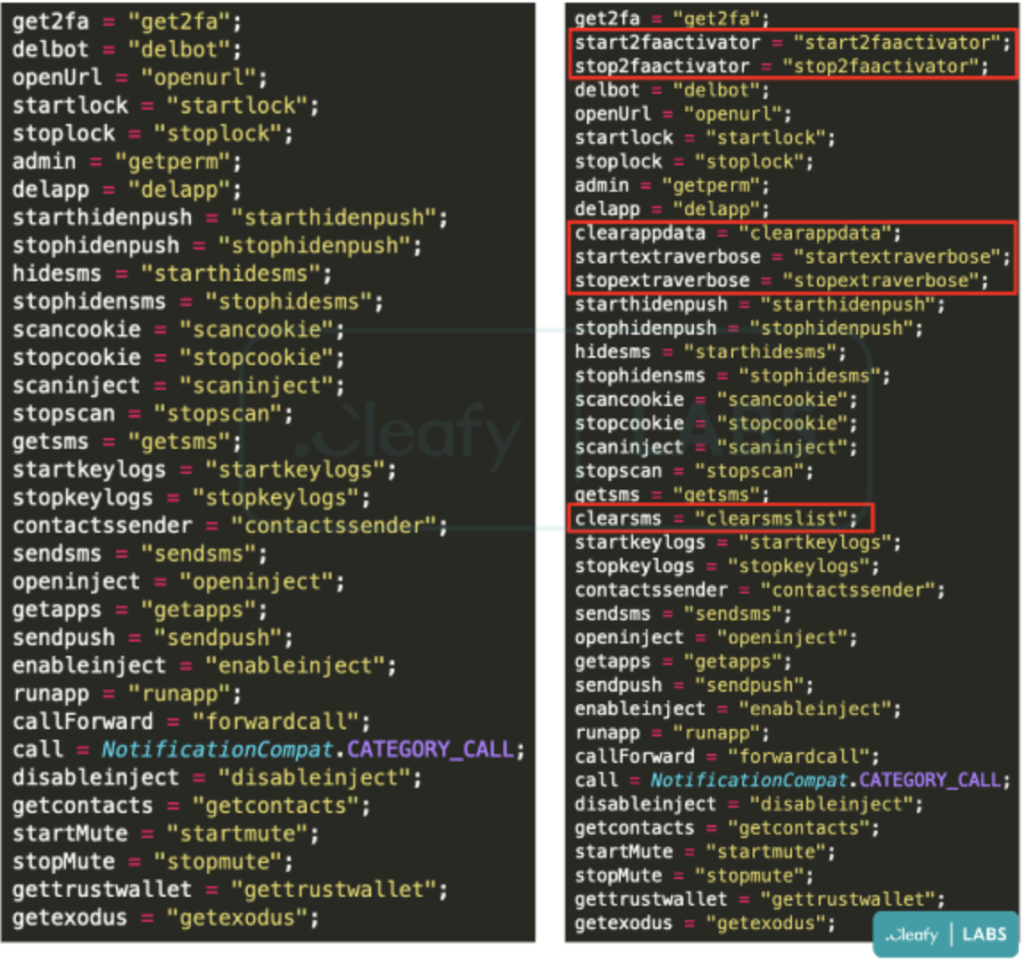
Apart from this, Android’s accessibility service can be abused by malware to read 2FA codes from SMS messages and Google Authenticator apps.
Here is a list of some updated and new functionalities that have been added:-
- The ability to delete SMS messages received
- Activate or stop the 2FA stealer module
- Ping a C2 server periodically to update itself.
The MaaS approach enables the threat actors to streamline their efforts in generating profits from malware by offering a pre-built infrastructure to their clients.
Without a VNC module, Nexus’ action range and capabilities are currently limited. Nexus is a threat that can infect hundreds of devices globally in accordance with the infection rate determined from multiple C2 panels.
Building Your Malware Defense Strategy – Download Free E-Book
Related Coverage:
- Weaponized Telegram and WhatsApp Apps Attack Android & Windows Users
- Weaponized Telegram and WhatsApp Apps Attack Android & Windows Users
- Beware! Fake ChatGPT Windows & Android Apps Deliver Dangerous Malware
- Android 14 Released – What’s New in Security
- PixPirate Android Malware Stealing Banking Passwords From Browsers
Read the full article here

