Pyongyang has been launching missiles with unprecedented frequency. Crypto asset theft by North Korean hackers is reportedly one of the sources funding their missile development.
The North Korean hacker group Lazarus has a worldwide reach. Its cyberattacks against crypto asset providers this year alone have caused an estimated tens of billions of yen worth of damage.
Although countries have strengthened countermeasures and sanctions in response, the damage continues to spread. The regime’s methods and money laundering schemes are getting increasingly sophisticated.
Japan Condemns North Korea by Name
On November 15, United States Homeland Security Secretary Alejandro Mayorkas stated the following in a written statement to the United States Senate Committee on Homeland Security and Government Affairs.
In the past two years alone, North Korea has “largely funded its weapons of mass destruction programs through cyber heists of cryptocurrencies and hard currencies totaling more than $1 billion USD (about ¥140 billion JPY).”
Lazarus and other hacker groups seem to be behind North Korea’s cyberattacks. An expert panel from the United Nations Security Council Sanctions Committee on North Korea noted in October that Lazarus is targeting crypto asset companies and exchanges. Japanese authorities have also started to use public attribution to condemn North Korea for the Lazarus attacks by name.
State-sponsored cyberattacks are usually aimed at information theft, such as military secrets and advanced technology. But North Korea is unique in that it obtains foreign currency illegally through cyberattacks. It is a powerful means of financing an economy wrecked by economic sanctions and the COVID-19 pandemic. According to the United Nations and the United States, the regime is also using the loot to fund its missile program.

Cyberattacks Escalate Under the Kim Jong Un Regime
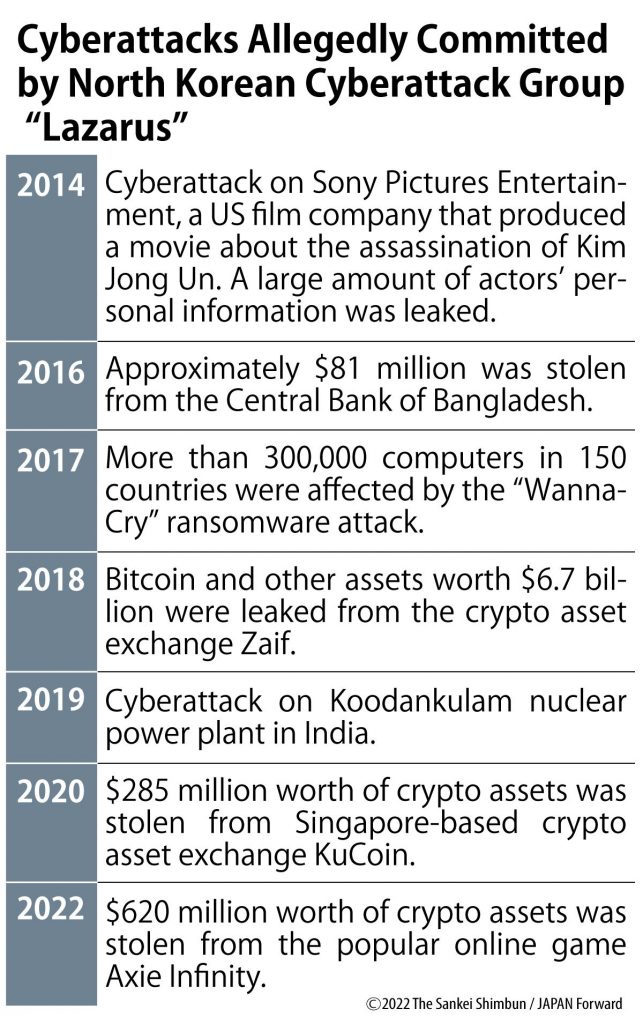
Lazarus became notorious in 2014 for the cyberattack on Sony Pictures Entertainment. The US film company was just about to release a movie about assassinating Kim Jong Un.
Then in 2016, a cyberattack that cost a Bangladeshi bank $81 million USD revealed that North Korea was targeting financial institutions and crypto assets. Since then, it has attacked crypto asset-related institutions one after another.
The FBI reported in April that North Korean hacker groups Lazarus and APT38 had stolen $620 million USD in crypto assets (about ¥87 billion JPY) through a cyberattack on the popular online game Axie Infinity. The heist is said to be one of the largest crypto asset thefts on record.
North Korea reportedly began training cyber organizations around 1986. In the 1990s, it trained about 100 IT professionals per year. By the early 2000s, North Korea had already begun its attack on other countries. In the wake of the King Jong Un regime, which began in 2011, North Korea’s cyberattacks to steal foreign currency went into full swing.
According to South Korea’s defense white paper for 2020, North Korea has expanded its cyber warfare capabilities with 6,800 cyber warfare personnel. Furthermore, it is reportedly recruiting gifted children from all over the country to develop human resources using special education programs.
Additionally, US cybersecurity firm Mandiant published a report in March on the hacker unit Lab 110. It works under Bureau 3, which is in charge of overseas intelligence, of the North Korean intelligence agency Reconnaissance General Bureau. The report suggests that the unit plays a central role in cyberattacks, and Lazarus reportedly works under this unit.

North Korean Hackers Send Targeted Emails
Katsuyuki Okamoto, a security evangelist at the cyber security company Trend Micro, explains how North Korea carries out its cyberattacks.
Targeted emails are a trademark of Lazarus’ cyberattacks. It sends phishing emails by impersonating an acquaintance or approaches targets on social media based on information made public on other social media platforms.
Okamoto urges caution. “Do not assume that it doesn’t concern you because you don’t have any state information or secrets. Many of us need to be vigilant because the regime targets financial institutions.”
Furthermore, Okamoto points out that it is difficult for individuals to defend themselves against the attacks because of their deceptiveness. He warns, “Check the sender’s address, do not open suspicious files, and be cautious of people who try to approach you through social media.”
RELATED:
(Read the report in Japanese at this link.)
Author: Misaki Owatari
Read the full article here


