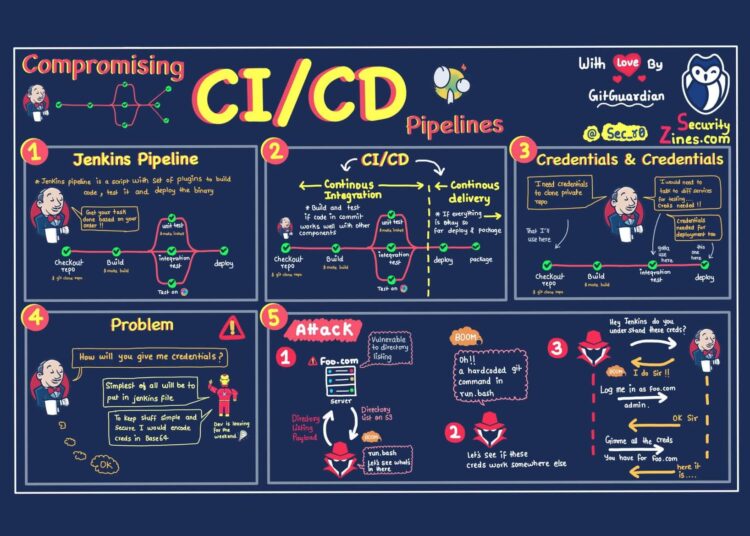
CI/CD pipelines require a number of permissions to function, and they handle infrastructure and application secrets in most organizations. As a result, whoever manages to gain unauthorized access to your CI/CD pipeline gains virtually absolute power to compromise your entire infrastructure or introduce malicious code. Therefore, you should give safeguarding CI/CD pipelines top priority.
What is a CI/CD Pipeline?
Applications are often delivered via a standardized, automated method known as a CI/CD pipeline. A CI/CD pipeline is a part of a larger toolchain that also includes automated testing, version management, and continuous integration, delivery, and deployment. The automation of the integration and delivery allows enterprises to deploy applications quickly and effectively.

While CI/CD pipelines help teams operate more quickly and with fewer chances for human mistakes, they also give bad actors a new attack surface to target. As a result, you should give safeguarding CI/CD pipelines top priority.
Secrets management is a critical aspect of CI/CD (Continuous Integration and Continuous Deployment) security. A secret is any sensitive information that should not be exposed, such as passwords, tokens, and private keys. In order to ensure the security of these secrets, it is important to follow best practices for secrets management.
Best Practices for Secret Management in CI/CD
The following best practices will help you strengthen your CI/CD security posture.
Use a Dedicated Secrets Management Tool
One of the most important best practices for secrets management is to use a dedicated secrets management tool. This tool should be designed specifically for the purpose of securely storing and managing secrets, and should be separate from other tools used in the CI/CD pipeline. This ensures that the secrets are stored in a secure location that is not accessible to unauthorized individuals or systems. Some popular secrets management tools include Hashicorp Vault, AWS Secrets Manager and Azure Key Vault.
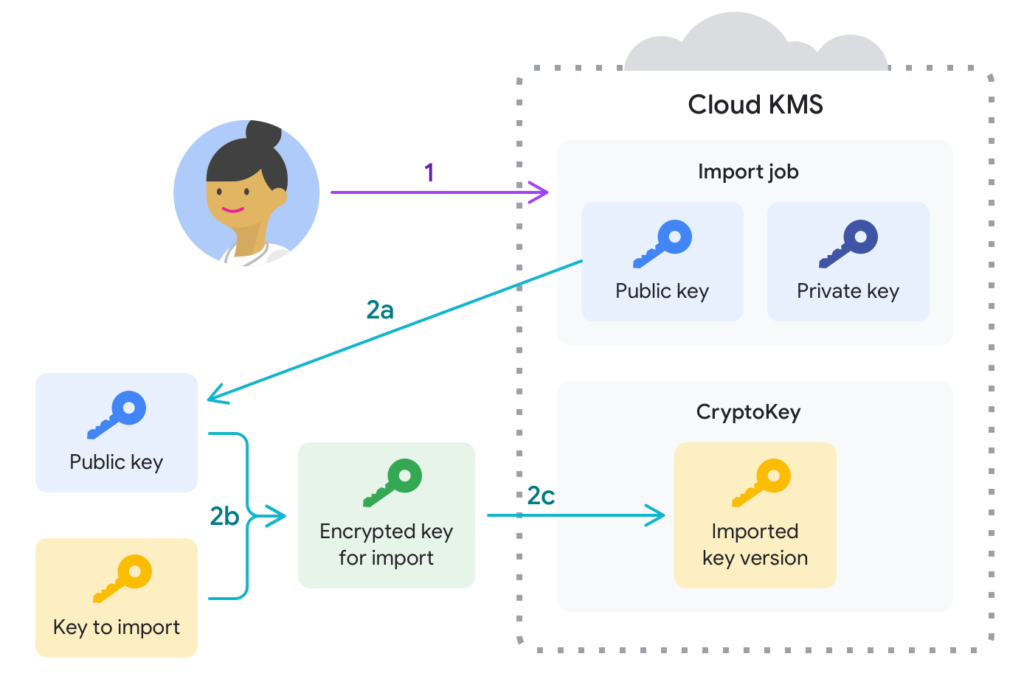
Encryption for All Secrets
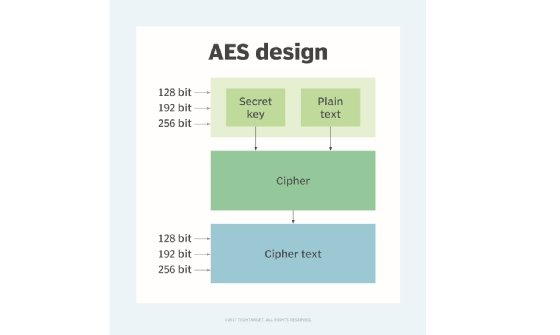
Another best practice is to use encryption for all secrets. This ensures that even if a secret is compromised, it will be difficult for an attacker to use it without the proper decryption key. Secrets should be encrypted both at rest and in transit. In addition, it is important to use a secure encryption algorithm, such as AES-256, and to rotate encryption keys regularly to ensure that the secrets remain secure over time.
Implement Access Controls
It is also important to implement access controls for secrets. This ensures that only authorized individuals or systems have access to the secrets. Access controls should be based on the principle of least privilege, meaning that users should only have access to the secrets that are necessary for their job function. In addition, it is important to track access to secrets, so that any unauthorized access can be detected and addressed.
Rotate Secrets Regularly
Another best practice is to rotate secrets regularly. This ensures that even if a secret is compromised, it will only be useful for a limited period of time. Secrets should be rotated at regular intervals, such
The Challenge of Managing Secrets in a CI/CD Pipeline
Managing secrets in a CI/CD pipeline can be a challenging task for organizations. A secret is any sensitive information that should not be exposed, such as passwords, tokens, and private keys. These secrets are used in various stages of the pipeline, from code integration to deployment, and their security is crucial to the overall security of the pipeline.
One of the main challenges of managing secrets in a CI/CD pipeline is ensuring that they are stored in a secure location that is not accessible to unauthorized individuals or systems. Secrets should be stored separately from the rest of the pipeline, and access to them should be restricted to only those who need it. This can be difficult to implement and maintain, especially in large and complex pipelines.
Another challenge is ensuring that secrets are encrypted both at rest and in transit. This is important to prevent unauthorized access, but it can be difficult to implement and maintain encryption across multiple stages of the pipeline. Additionally, it is important to rotate encryption keys regularly to ensure that the secrets remain secure over time.
Implementing access controls for secrets is also a challenge. This involves ensuring that only authorized individuals or systems have access to the secrets, based on the principle of least privilege. This can be difficult to implement and maintain, especially in large and complex pipelines. It is also important to track access to secrets so that any unauthorized access can be detected and addressed.
Another challenge is rotating secrets regularly. This involves regularly changing the secrets to prevent them from being compromised. This can be difficult to implement and maintain, especially in large and complex pipelines.
Overall, managing secrets in a CI/CD pipeline can be a challenging task for organizations. Ensuring that secrets are stored securely, encrypted, and accessible only to authorized individuals or systems, and rotated regularly is crucial for the overall security of the pipeline. However, implementing and maintaining these practices can be difficult and time-consuming, especially in large and complex pipelines.
Conclusion
Integrating security before, inside, and after pipelines is crucial because CI/CD is one of the main DevOps methods. Organizations must take precautions against attackers accessing CI/CD infrastructure to thwart their attempts to breach the organization and introduce harmful bugs into their apps. This is particularly important as attackers are increasingly focusing their attention on development environments.
Read the full article here