KEY TAKEAWAYs
- The primary motivation for threat actors targeting the healthcare sector in 2022 appeared to be financial, as the sector was significantly affected by data breaches and ransomware attacks.
- According to Cyber Risk Analytics (CRA), at time of writing, the healthcare sector has experienced 556 data breaches, which have led to the compromise of over 65 million records.
- Ransomware remained a significant threat for healthcare organizations this year. Like in previous years, ransomware gangs targeted hospitals or other treatment facilities knowing that minimizing downtime could have life-or-death consequences, which may make an entity more apt to pay the demanded ransom.
The healthcare landscape
According to a recent study, more than 20 percent of surveyed healthcare organizations experienced an increase in mortality rates due to cyberattacks in 2022. Of the nearly 650 organizations that were included in the study, 89 percent reported at least one attack over the last twelve months—reporting 43 cyberattacks on average. Additionally, 20 percent of the participants reported having been victims of cloud compromise, supply chain attacks, ransomware, or phishing.
In our 2020 and 2021 Healthcare Year In Review reports, we highlighted the impact that COVID-19 had on the healthcare sector. This year, our analysts still observed general fraud related to the pandemic, like the advertising of COVID-related datasets. However, looking at 2022, the sector was less impacted by the pandemic than in previous years.
Impact of data breaches on healthcare
According to data from CRA, the healthcare and social assistance sector was the second most impacted sector by data breaches this year globally—following finance and insurance. Year to date, the healthcare sector has experienced 556 breaches, resulting in over 65 million total breached records, according to CRA. These numbers are expected to grow as impacted entities retroactively publicly disclose breaches.
The majority of the impacted entities were hospitals, followed by ambulatory health care services and social services.
Impact of cyberattacks on healthcare
Healthcare-related advertisements and solicitations remained popular among threat actor communities within this year. Threat actors continued to buy and sell network access to healthcare organizations, pharmaceutical companies, insurance organizations, and third-party resources that store PHI, such as patient data, “fullz” (full packages of personally identifiable information), COVID-19 passports, prescriptions, insurance information, and Medicare data.
Cybercriminals continue to breach data from healthcare organizations to trade on underground markets and forums. The leading forums for discussing such data included mid-tier English-language hacking forum Breach Forums, and top-tier Russian-language hacking forum Exploit. Breach Forums quickly became the go-to English language hacking forum for threat actors attempting to buy and sell such data in 2022, accounting for nearly 30 percent of all observed healthcare-related advertisements.
Raid Forums was the third most popular forum for healthcare-related information, although it was seized by US law enforcement in late February 2022.
This year, the United States was the region most impacted by advertisements for and solicitations of healthcare-related information.
Ransomware’s impact on healthcare
According to the FBI’s Internet Crime Complaint Center (IC3), the healthcare and public health (HPH) sector accounts for 25 percent of ransomware complaints across all sixteen critical infrastructure sectors. Ransomware groups tend to target organizations that store and maintain high-value sensitive information. Healthcare organizations are considered prime targets, as they are more likely to pay a ransom quickly in order to restore networks, services, and treatments.
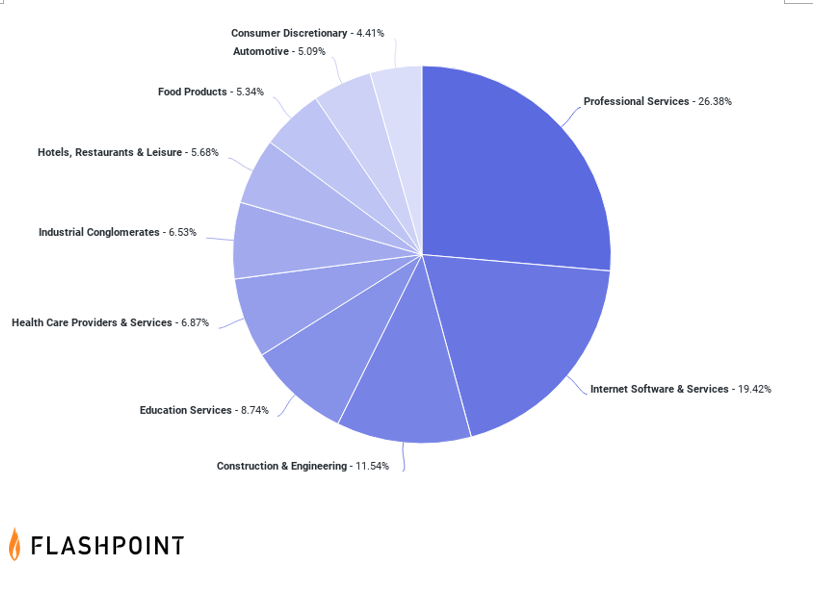
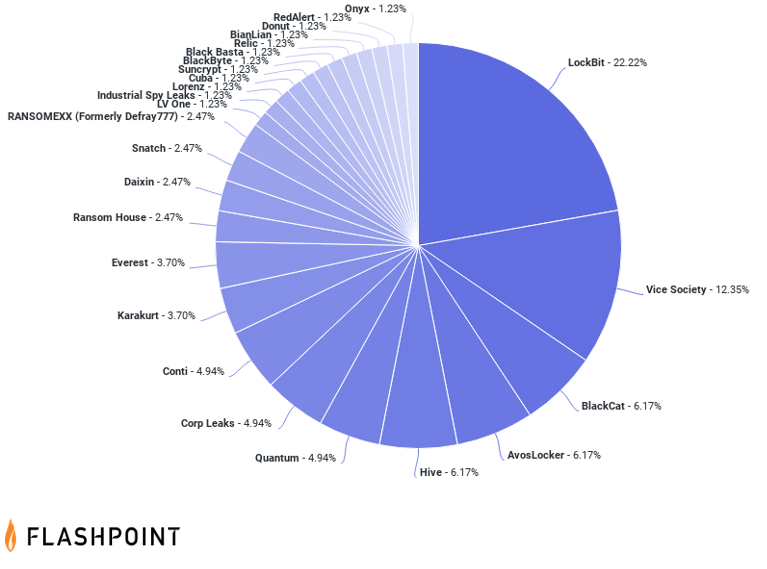
Flashpoint’s data on publicly known ransomware attacks showed that 6.78 percent of attacks reported in 2022 affected the healthcare sector, making it the fifth most targeted sector. “LockBit” was the most common group to target these organizations, conducting nearly a quarter of healthcare ransomware attacks in 2022.
Internet of medical things
A major concern for healthcare organizations is the growing attack surface created by the Internet of Things (IoT)—particularly medical devices. Healthcare organizations have, on average, 26,000 network-connected devices—each possibly containing exploitable vulnerabilities. Unsecured medical devices, such as heart rate monitors, and mobile apps are especially a top security concern. According to a recent study, the more connected medical devices an organization has, the more likely it is to experience a cyberattack.
The study further states that 57 percent of IT security practitioners say they do not always modify the default credentials for connected devices before issuing them to employees, and 5 percent never modify them. Furthermore, 68 percent of organizations reported that they do not routinely patch devices or update firmware. However, it is important to note that the failure to do so sometimes is because the product runs on legacy platforms which are often unsupported. In other cases, it is due to an absence of connected medical device monitoring solutions, such as antivirus or endpoint protection tools—further highlighting the importance of comprehensive vulnerability intelligence.
Flashpoint helps healthcare organizations safeguard assets and data
Flashpoint’s suite of actionable intelligence solutions enables healthcare organizations to proactively identify and mitigate cyber and physical risk that could imperil people, places, and assets. To unlock the power of great threat and vulnerability intelligence, get started with a free Flashpoint trial.
Read the full article here