A post-exploitation tampering technique has been discovered that allows the malware to visually trick the user into thinking their iPhone is in Lockdown Mode.
While iOS devices with Lockdown Mode have a smaller attack surface, it’s crucial to keep in mind that Lockdown Mode does not prevent malware from executing after a device has been compromised.

Lockdown Mode does not identify malware that has already been installed, it does not act as antivirus software, and it has no effect on the ability to spy on a device that has already been infiltrated.
Truly, its effectiveness lies in limiting the number of entry points that an attacker can exploit before an attack occurs.
False Sense of Security with Lockdown Mode
In September 2022, Apple implemented Lockdown Mode in reaction to an increase in worldwide cyberattack campaigns.
To prevent possible attackers from accessing all functionality, Lockdown Mode reduces it. Despite being simple, this strategy is strong because the less code you expose, the fewer opportunities attackers have to exploit weaknesses in your device.
iOS 16 or later, iPadOS 16 or later, watchOS 10 or later, and macOS Ventura or later all support lockdown mode. WatchOS 10, macOS Sonoma, iPadOS 17, and iOS 17 all offer additional protection.
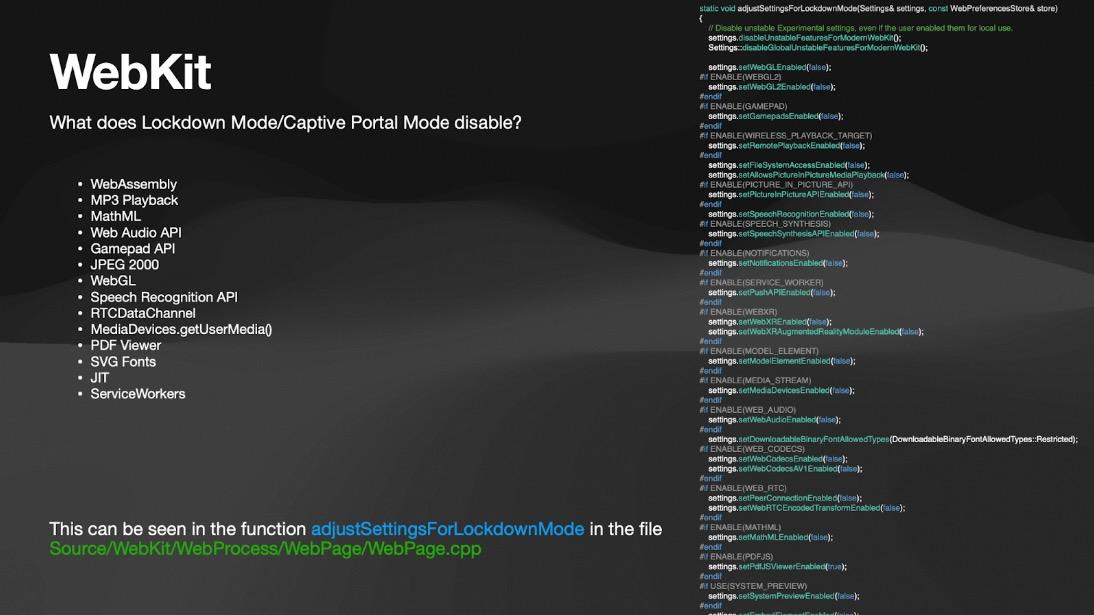
Certain file formats will no longer be supported when Lockdown Mode is activated, mostly because of their history of exploitation. Additionally, it will turn off convenient features like the ability to preview URLs received through Messages, turn off shared albums, stop configuration profile installations, and block enrollment in mobile device management (MDM) software.
“While Lockdown Mode has proven its effectiveness in certain scenarios, our evaluation of Lockdown Mode emphasizes that it won’t stop an attack that has already been initiated on the device”, Jamf Threat Labs said in a report shared with Cyber Security News.
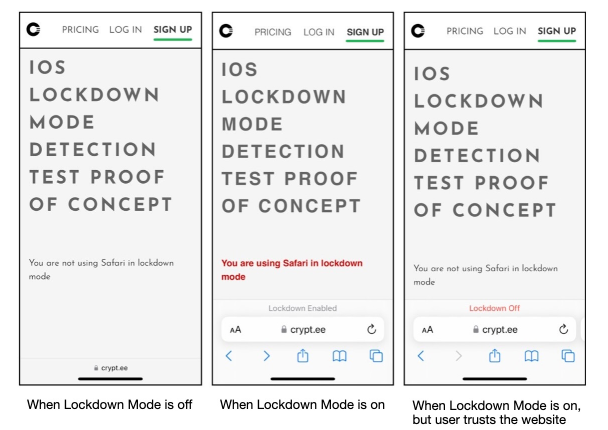
“When Lockdown Mode is enabled, your device won’t function like it typically does. To reduce the attack surface that potentially could be exploited by highly targeted mercenary spyware, certain apps, websites, and features are strictly limited for security and some experiences might not be available at all”, according to Apple.
There is a warning for iPhone users: locking down won’t stop malware that has already gained access to the system if your device has already been compromised.
Rather than adding more security mechanisms to stop malicious payloads from being executed, Lockdown Mode’s main goal is to decrease potential attack vectors.
Read the full article here